NIST’s first post-quantum standards
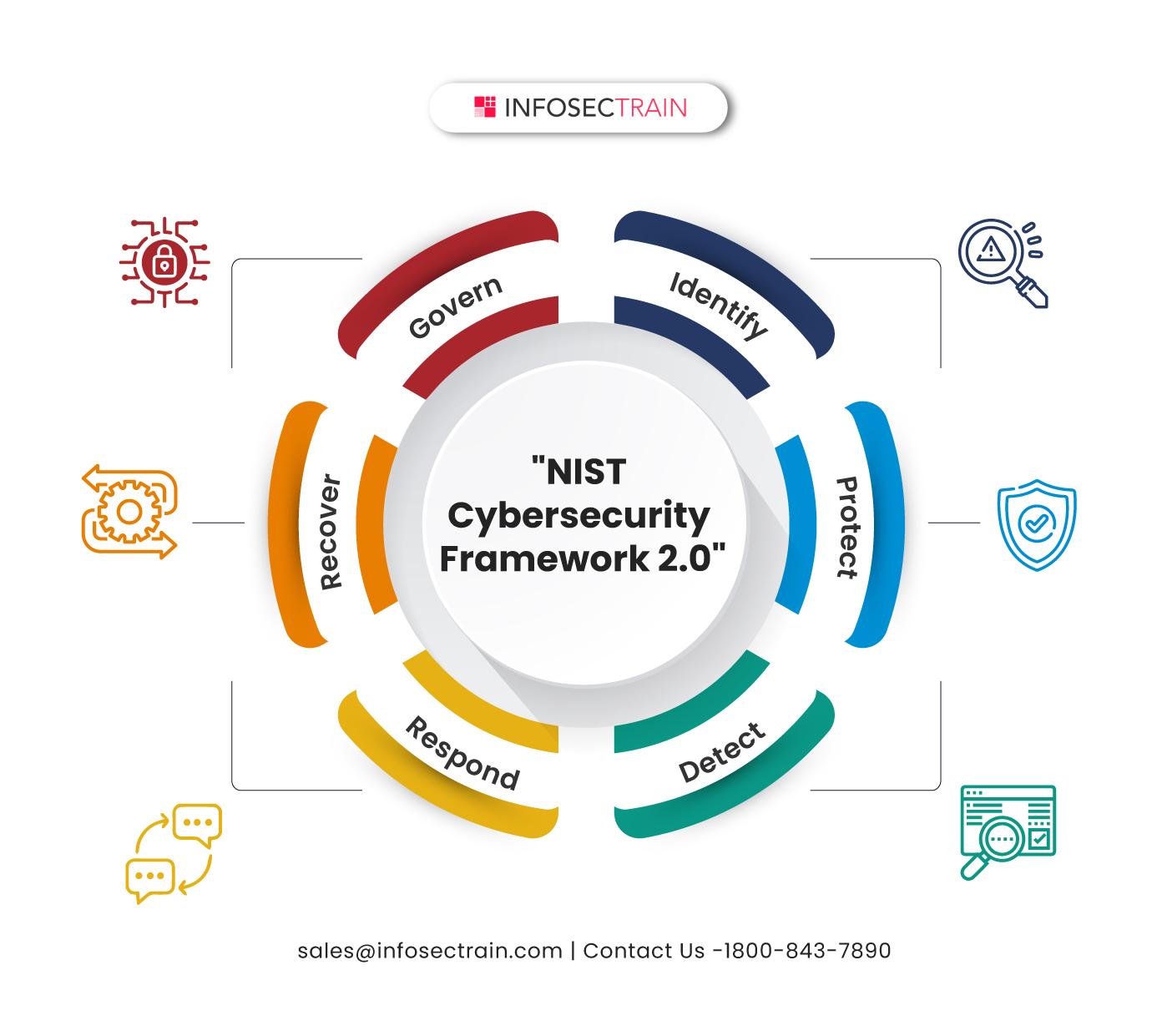
NIST has officially released its first post-quantum standards, marking a significant milestone in the world of cryptography. These standards aim to protect data from potential threats posed by quantum computers in the future.
Read more
Introducing Automatic SSL/TLS: securing and simplifying origin connectivity
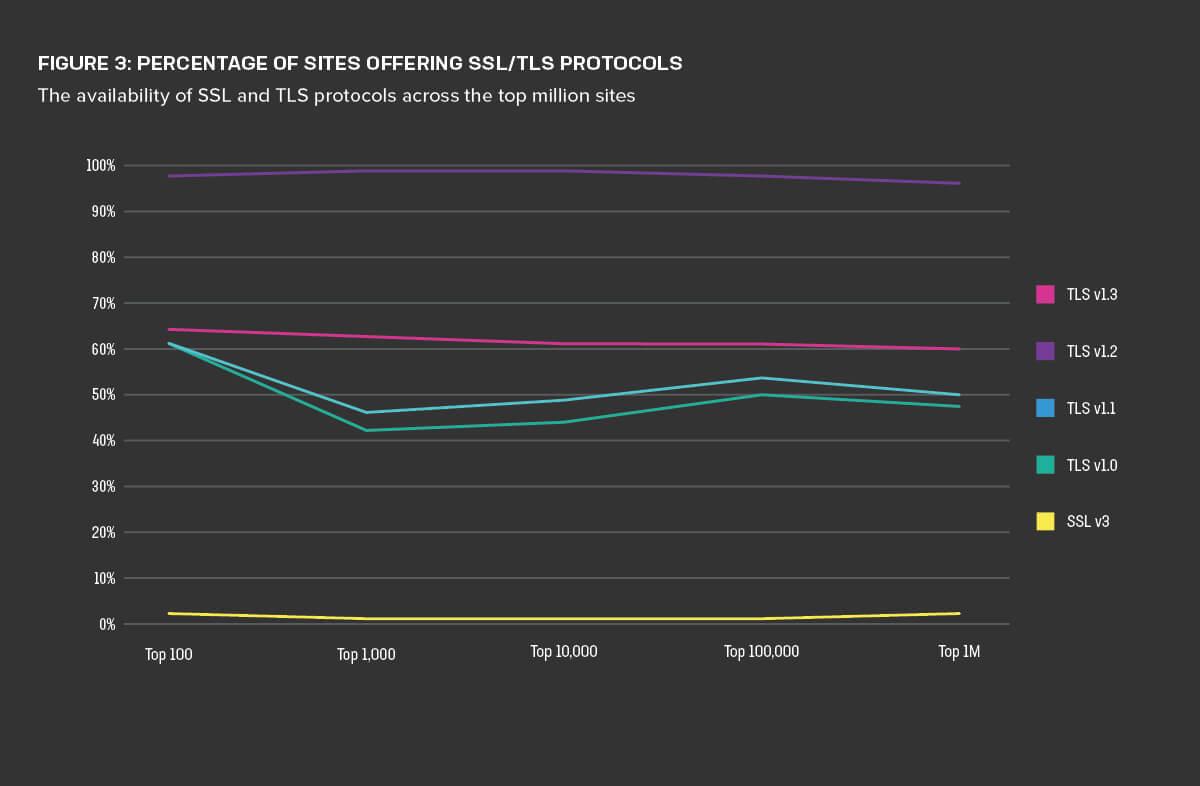
In the ever-evolving landscape of cybersecurity, the introduction of Automatic SSL/TLS is revolutionizing the way we secure and simplify origin connectivity. With this game-changing technology, organizations can rest assured that their data is protected without the hassle of manual configurations.
Read more
Summer 2024 weather report: Cloudflare with a chance of Intern-ets

As we look ahead to the summer of 2024, the forecast is shaping up to be a mix of Cloudflare with a chance of Intern-ets. With fluctuating internet speeds and possible disruptions, stay prepared for a season of digital unpredictability.
Read more
How to Spot and Stop a DDoS Attack

As the digital landscape continues to evolve, DDoS attacks have become more prevalent. Learn how to recognize the signs and take action against these malicious threats before they disrupt your online presence.
Read more
What Is Brotli Compression? | How Does It Work?
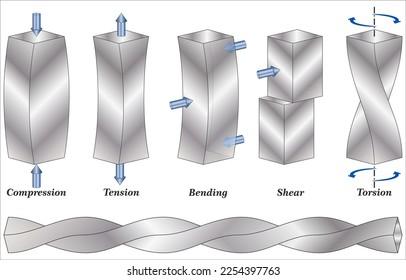
Welcome to the world of Brotli compression! This innovative technology promises faster loading times and reduced bandwidth usage for websites. But how does it actually work? Let's dive into the details and uncover the magic behind Brotli compression.
Read more
What Is Edge Artificial Intelligence? How Does Edge AI Work?
Edge Artificial Intelligence is revolutionizing technology by bringing AI capabilities directly to devices such as smartphones and industrial machines. By processing data locally, Edge AI enhances speed, privacy, and efficiency. But how does it work? Let's dive in.
Read more
What Is the OSI Model? | How Does It Work?

The OSI model, short for Open Systems Interconnection model, is a standardized framework that defines the functions of a telecommunication or computing system into seven abstract layers. Each layer serves a specific purpose, enabling seamless communication between devices. Let's delve into how this intricate model works to facilitate data transfer across networks.
Read more
What Is TCP DDoS Protection? | How Does It Work?

TCP DDoS protection is a crucial defense mechanism against harmful cyber attacks. By monitoring and filtering incoming traffic, it safeguards the network from overwhelming malicious requests. Let's delve into the intricacies of how this technology operates to keep our data safe.
Read more
How to Detect and Stop Bad Bots

Discover the sneaky world of bad bots and learn how to spot and stop them in their tracks. From analyzing website traffic patterns to implementing advanced security measures, we've got you covered in the battle against malicious bots.
Read more









