In the vast landscape of cybersecurity, one term that constantly looms large is DDoS attacks. These malicious assaults can cripple websites, networks, and servers, causing downtime, loss of revenue, and serious headaches for businesses. In the ever-evolving battle against such threats, TCP DDoS protection has emerged as a vital line of defense. But what exactly is it, and how does it work? Let’s delve into the world of TCP DDoS protection to find out.
Table of Contents
- Understanding TCP DDoS Attacks
- Importance of TCP DDoS Protection
- Mechanisms of TCP DDoS Protection
- Tips for Implementing TCP DDoS Protection
- Q&A
- To Wrap It Up

Understanding TCP DDoS Attacks
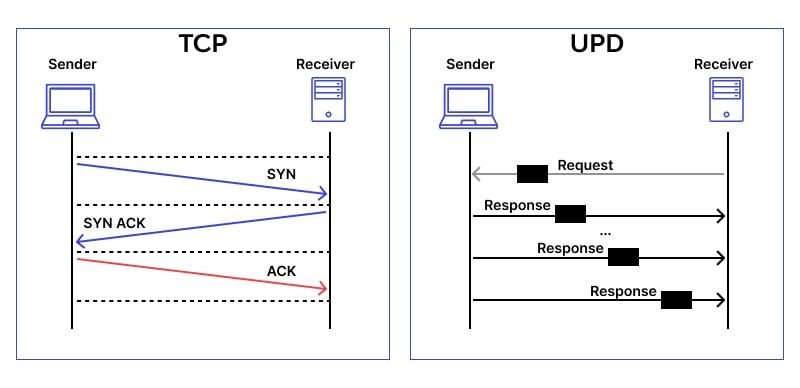
One of the most common forms of cyber attacks on websites and online services is the TCP DDoS attack. This type of attack targets the Transmission Control Protocol (TCP) to overload a server’s resources and make the website or service inaccessible to legitimate users. TCP DDoS attacks are particularly dangerous because they can be difficult to detect and mitigate without proper protection.
TCP DDoS protection works by filtering incoming network traffic to identify and block suspicious or malicious packets before they reach the server. This process helps to prevent the server from becoming overwhelmed by the massive volume of requests generated by the attackers. By using advanced algorithms and analysis, TCP DDoS protection solutions can effectively defend against these types of attacks and ensure the availability and performance of websites and services for legitimate users.
Importance of TCP DDoS Protection
One important aspect of protecting your website or online service from potential threats is implementing TCP DDoS protection. TCP (Transmission Control Protocol) DDoS attacks can wreak havoc on your network by overwhelming it with malicious traffic, causing downtime and disrupting user experience. By putting in place effective TCP DDoS protection measures, you can mitigate the risks associated with these types of attacks and keep your online presence secure.
So, how does TCP DDoS protection work? Essentially, TCP DDoS protection solutions monitor and analyze incoming traffic to identify and filter out any suspicious or malicious packets. This process helps to ensure that only legitimate traffic is allowed to pass through to your network, while malicious traffic is blocked before it can cause any harm. By employing advanced algorithms and detection techniques, TCP DDoS protection helps to maintain the stability and availability of your online services, even in the face of potential DDoS attacks.

Mechanisms of TCP DDoS Protection
TCP DDoS protection utilizes various mechanisms to safeguard against distributed denial-of-service attacks targeting TCP connections. One key method is through rate limiting, where incoming TCP traffic is monitored and restricted to prevent overload on the server. Additionally, deep packet inspection is employed to analyze the content of TCP packets and identify suspicious patterns indicative of a DDoS attack.
Another crucial aspect of TCP DDoS protection is the use of SYN cookies to mitigate SYN flood attacks. SYN cookies help in verifying legitimate connection requests while filtering out malicious ones, thus ensuring the server’s resources are not consumed by fake TCP connections. Furthermore, TCP DDoS protection may also involve the implementation of session tracking mechanisms to monitor and manage the state of TCP connections in real-time, enabling prompt detection and mitigation of potential DDoS threats.
| Key |
|---|
| Rate Limiting |
| Deep Packet Inspection |
| SYN Cookies |
| Session Tracking |
Tips for Implementing TCP DDoS Protection
When it comes to protecting your network from TCP DDoS attacks, there are a few key tips to keep in mind. First and foremost, make sure to implement robust firewall rules that can detect and block malicious traffic targeting your TCP ports. This will help prevent attackers from overwhelming your network with spoofed TCP packets.
Additionally, consider deploying a dedicated TCP DDoS protection solution that can intelligently analyze incoming traffic patterns and mitigate attacks in real-time. By leveraging technologies such as rate limiting, packet inspection, and anomaly detection, you can effectively defend against TCP DDoS attacks before they impact your network’s performance. Remember, proactive monitoring and regular updates to your TCP DDoS protection strategy are crucial for staying ahead of evolving threats in the ever-changing cybersecurity landscape.
Q&A
Q: What is TCP DDoS protection and why is it important?
A: TCP DDoS (Distributed Denial of Service) protection is a security measure designed to defend against malicious attacks that overload a network with traffic. It is crucial in preventing downtime and maintaining the availability of online services.
Q: How does TCP DDoS protection work?
A: TCP DDoS protection works by analyzing incoming traffic and identifying patterns that indicate a potential attack. It then filters out malicious traffic while allowing legitimate traffic to pass through, helping to keep the network operating smoothly.
Q: What are some common techniques used in TCP DDoS protection?
A: Some common techniques used in TCP DDoS protection include rate limiting, IP blocking, and SYN flood protection. These methods help to mitigate the impact of DDoS attacks and keep networks safe from harm.
Q: How can businesses benefit from implementing TCP DDoS protection?
A: Businesses can benefit from implementing TCP DDoS protection by safeguarding their online services and preventing costly downtime. By having robust protection in place, they can ensure that their networks remain secure and operational even in the face of malicious attacks.
Q: Are there any challenges associated with TCP DDoS protection?
A: While TCP DDoS protection is effective in combating attacks, there can be challenges in terms of cost and complexity of implementation. However, the benefits of protecting against DDoS attacks far outweigh these challenges, making it a worthwhile investment for businesses.
To Wrap It Up
TCP DDoS protection is an essential tool in safeguarding your network from malicious attacks that can disrupt your services and compromise your security. By analyzing and filtering incoming traffic, TCP DDoS protection works to mitigate the impact of DDoS attacks and ensure the uninterrupted operation of your online assets. With the constantly evolving landscape of cyber threats, investing in robust TCP DDoS protection is crucial for any organization looking to stay ahead of potential attacks and protect their digital infrastructure. Stay informed, stay protected, and keep your online presence secure with TCP DDoS protection.










