In a world where digital connectivity reigns supreme, securing access to critical infrastructure is paramount. Enter SSH, a trusted protocol for establishing secure connections over unsecured networks. In this article, we will explore the basics of SSH and how it plays a crucial role in safeguarding the integrity of our infrastructure. Join us on this journey as we delve into the world of SSH and its implications for the future of network security.
Table of Contents
- Heading 1: Understanding the Importance of SSH Access for Infrastructure Security
- Heading 2: Exploring the Benefits of Implementing SSH for Secure Remote Communication
- Heading 3: Best Practices for Setting Up SSH Access to Safeguard Your Infrastructure
- Heading 4: Enhancing Security Measures with SSH Key Management and Authentication Strategies
- Q&A
- In Summary
Heading 1: Understanding the Importance of SSH Access for Infrastructure Security
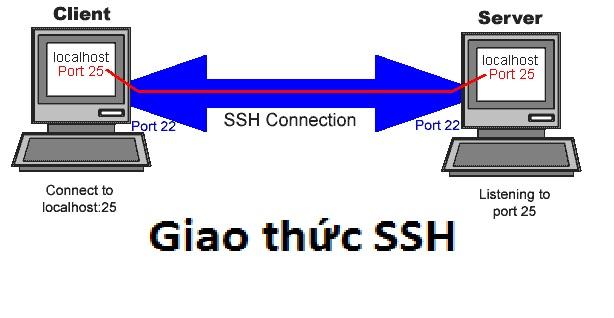
Access control is an essential aspect of infrastructure security. Secure Shell (SSH) access plays a crucial role in maintaining the integrity and confidentiality of data within a network. By utilizing SSH, organizations can securely access and manage their servers, routers, and other devices remotely. This encrypted protocol provides a secure channel for data transmission, preventing unauthorized access and potential cyber threats.
Additionally, SSH access allows for secure file transfers and authentication between systems. With SSH, administrators can authenticate their identity using public key cryptography, adding an extra layer of security to their infrastructure. By implementing strong password policies and limiting access privileges, organizations can enhance their overall security posture and mitigate the risk of unauthorized access. Understanding the importance of SSH access is vital for safeguarding sensitive data and ensuring the continuity of business operations.
Heading 2: Exploring the Benefits of Implementing SSH for Secure Remote Communication
Secure Shell (SSH) is a powerful tool that offers encrypted communication between two systems, providing a secure way to access and manage remote servers. By implementing SSH for remote communication, you can significantly enhance the security of your infrastructure and protect sensitive data from unauthorized access.
Some of the key benefits of using SSH for secure remote communication include:
- Encrypted Data Transmission: SSH encrypts all data exchanged between the client and server, ensuring that sensitive information remains secure during transmission.
- Authentication: SSH uses public key cryptography to authenticate the identity of both the client and server, adding an extra layer of security to the communication process.
- Remote Access: With SSH, you can securely access and manage remote servers from anywhere in the world, making it an essential tool for system administrators and IT professionals.
Heading 3: Best Practices for Setting Up SSH Access to Safeguard Your Infrastructure
Setting up SSH access is crucial for safeguarding your infrastructure against unauthorized access and potential security threats. By following best practices, you can ensure that only authorized users can access your servers and network systems.
Some key best practices for setting up SSH access include:
- Using strong passwords or SSH keys for authentication
- Disabling root login to prevent unauthorized access
- Implementing firewall rules to restrict access to specific IP addresses
- Regularly updating SSH software to patch known vulnerabilities
By following these best practices, you can strengthen the security of your infrastructure and protect your sensitive data from potential cyber attacks.
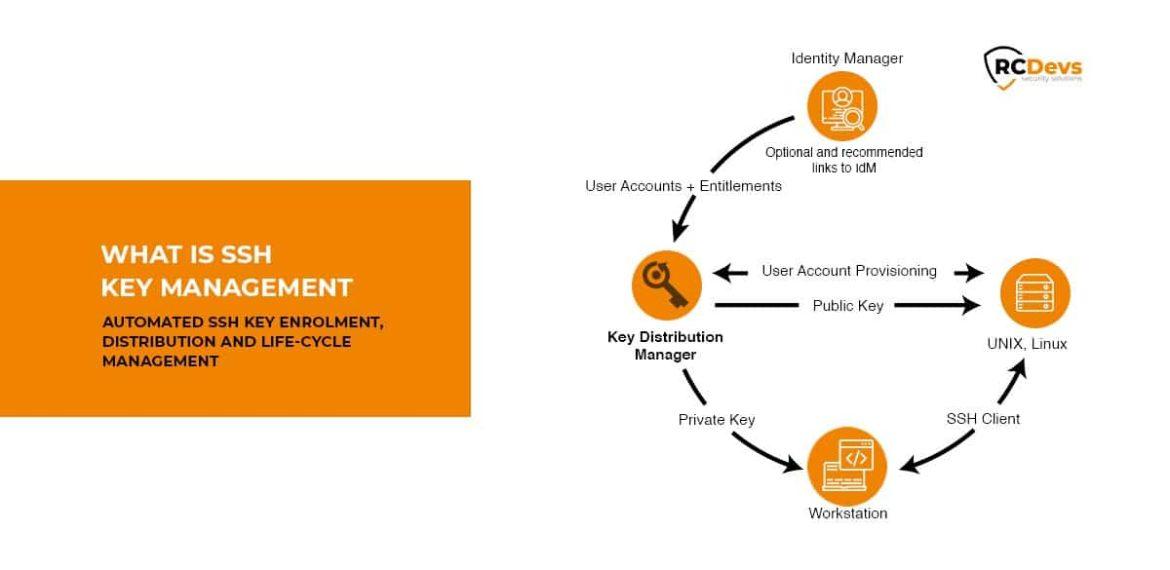
Heading 4: Enhancing Security Measures with SSH Key Management and Authentication Strategies
When it comes to securing your infrastructure, SSH key management and authentication strategies are essential tools to enhance security measures. By utilizing SSH keys, you can create a more secure and efficient way to access your servers and network devices. This cryptographic network protocol provides a secure channel for data communication over an unsecured network, reducing the risk of unauthorized access and potential security breaches.
With proper SSH key management, you can ensure that only authorized users have access to your infrastructure, minimizing the risk of malicious attacks. By implementing strong authentication strategies, such as two-factor authentication and regular key rotation, you can further enhance the security of your systems. When it comes to protecting your sensitive information and critical assets, investing in SSH key management is a proactive step towards safeguarding your infrastructure from potential threats.
Q&A
Q: What is Access for Infrastructure?
A: Access for Infrastructure is a tool that allows secure access to servers and other infrastructure components using SSH.
Q: What is SSH?
A: SSH (Secure Shell) is a network protocol that allows secure communication between two devices, typically used for remote access to servers.
Q: How does Access for Infrastructure enhance SSH usage?
A: Access for Infrastructure provides a centralized platform for managing SSH access, including user authentication, permissions, and monitoring.
Q: What are the benefits of using Access for Infrastructure with SSH?
A: By using Access for Infrastructure with SSH, organizations can improve security, streamline access management, and ensure compliance with industry regulations.
Q: How easy is it to implement Access for Infrastructure?
A: Access for Infrastructure is designed to be user-friendly, with simple setup and configuration processes to help organizations quickly integrate it into their existing infrastructure.
Q: Can Access for Infrastructure be customized for specific organizational needs?
A: Yes, Access for Infrastructure offers customization options to tailor access controls and policies to meet the unique requirements of different organizations.
Q: What security measures does Access for Infrastructure have in place to protect SSH access?
A: Access for Infrastructure includes features such as multi-factor authentication, role-based access control, and audit logs to enhance security and prevent unauthorized access.
Q: How does Access for Infrastructure support scalability for growing organizations?
A: Access for Infrastructure is designed to scale with organizations, providing flexibility to add new users, servers, and permissions as needed without compromising security or performance.
In Summary
SSH is a powerful tool that provides secure access to infrastructure, allowing users to manage and maintain their systems with ease. By understanding the basics of SSH, users can harness its full potential to streamline their workflows and enhance their security measures. So, whether you’re a seasoned sysadmin or a newcomer to the world of infrastructure management, incorporating SSH into your toolkit is a decision you won’t regret. Embrace the power of SSH and take your infrastructure management to new heights. Happy networking!