In a digital world plagued by constant threats and vulnerabilities, the need for robust security measures is paramount. Enter Log Explorer, a groundbreaking solution that allows users to monitor security events without relying on third-party storage. With its innovative approach, Log Explorer empowers organizations to stay one step ahead of potential threats, all while maintaining control over their sensitive data. In this article, we will delve into the features and benefits of Log Explorer, and explore how it is revolutionizing the way we approach cybersecurity.
Table of Contents
- Overview of Log Explorer’s Security Event Monitoring Capabilities
- Advantages of Using Log Explorer for Security Event Monitoring
- How Log Explorer Eliminates the Need for Third-Party Storage Solutions
- Best Practices for Maximizing Security Event Monitoring with Log Explorer
- Q&A
- Final Thoughts
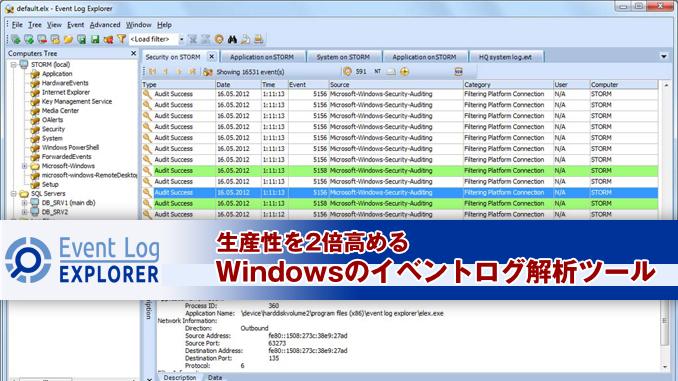
Overview of Log Explorer’s Security Event Monitoring Capabilities
Log Explorer offers robust security event monitoring capabilities that allow you to track and analyze security incidents in real-time, all without the need for third-party storage. With Log Explorer, you can monitor a wide range of security events across your network, including logins, file access, changes to system settings, and more. By centralizing your security event monitoring within Log Explorer, you can easily spot suspicious activity and take immediate action to protect your network.
With Log Explorer’s intuitive dashboard, you can quickly view and analyze security events as they occur, gaining valuable insights into potential threats to your network. The platform also offers customizable alerts that notify you of critical security events in real-time, ensuring that you can respond promptly to any security incidents. By leveraging Log Explorer’s comprehensive security event monitoring capabilities, you can proactively safeguard your network against cyber threats and ensure the integrity of your data.
Advantages of Using Log Explorer for Security Event Monitoring
Log Explorer offers a unique solution for monitoring security events without the need for third-party storage. By utilizing its built-in storage capabilities, users can keep all their logs in one centralized location, eliminating the need for additional storage solutions. This not only simplifies the monitoring process but also ensures that sensitive security event data is kept secure and easily accessible.
With Log Explorer, users can quickly and efficiently analyze security events through its user-friendly interface. The tool provides easy-to-read visualizations and reports, allowing users to identify potential threats and vulnerabilities promptly. Additionally, Log Explorer offers real-time monitoring capabilities, enabling users to respond to security events as they happen. By using Log Explorer for security event monitoring, users can enhance their overall security posture and better protect their systems and data.
How Log Explorer Eliminates the Need for Third-Party Storage Solutions
Log Explorer revolutionizes the way organizations monitor security events by offering a comprehensive solution that eliminates the need for third-party storage. With Log Explorer, you can now securely store and analyze logs without relying on external storage solutions, saving both time and resources. By streamlining the process, organizations can focus on identifying and addressing security threats more efficiently.
With Log Explorer, access to real-time security event monitoring is made easy, thanks to its user-friendly interface. The platform offers advanced search capabilities, customizable dashboards, and automated alerts to ensure that any suspicious activity is promptly detected and mitigated. By consolidating storage and monitoring functions into one comprehensive tool, Log Explorer empowers organizations to take control of their security posture without the added complexity of third-party solutions.

Best Practices for Maximizing Security Event Monitoring with Log Explorer
When it comes to maximizing security event monitoring with Log Explorer, there are several best practices to keep in mind. One key strategy is to regularly review and analyze logs to identify any unusual patterns or suspicious activities. By staying vigilant and proactive in monitoring security events, you can detect potential threats before they escalate.
Another important practice is to set up alerts and notifications within Log Explorer to immediately notify you of any critical security events. This way, you can take swift action to address any security breaches or vulnerabilities. Additionally, regularly updating and fine-tuning your monitoring settings can help ensure that you are capturing all relevant security events and minimizing false positives.
Q&A
Q: What is Log Explorer and how does it work?
A: Log Explorer is a tool that allows users to monitor security events on their systems without relying on third-party storage. It works by collecting and analyzing log data directly from the user’s own servers.
Q: Why is it important to monitor security events?
A: Monitoring security events is crucial for detecting and preventing potential security breaches or unauthorized access to sensitive data. By staying vigilant and proactive, users can better protect their systems from cyber threats.
Q: How does Log Explorer help users maintain control over their data?
A: Log Explorer eliminates the need to store log data on third-party servers, reducing the risk of unauthorized access or data breaches. This gives users more control and peace of mind when it comes to protecting their sensitive information.
Q: What sets Log Explorer apart from other monitoring tools?
A: One of the key features that sets Log Explorer apart is its ability to analyze log data without relying on third-party storage. This not only enhances security but also gives users more autonomy over their data.
Q: How can users benefit from using Log Explorer?
A: Users can benefit from using Log Explorer by having a reliable and secure tool for monitoring security events without compromising their data privacy. It provides peace of mind and a proactive approach to cybersecurity.
Final Thoughts
Log Explorer offers a secure and efficient solution for monitoring security events without relying on third-party storage. By keeping all logs within your own infrastructure, you can have peace of mind knowing that your sensitive data is not being shared with external parties. With its user-friendly interface and powerful features, Log Explorer is a valuable tool for keeping your organization protected from potential threats. Say goodbye to worries about data privacy and start exploring the possibilities with Log Explorer today.










