In today’s digital age, Application Programming Interfaces (APIs) play a crucial role in enabling seamless communication and interoperability between different software systems. However, with increased usage and reliance on APIs, the risk of abuse and security breaches has also risen exponentially. To combat this growing threat, researchers have turned to innovative solutions such as sequence learning and variable order Markov chains. By leveraging these cutting-edge techniques, businesses can now protect their APIs from abuse and ensure the integrity of their data and systems.
Table of Contents
- Understanding the Threat of API Abuse
- Implementing Sequence Learning for Enhanced Security
- Utilizing Variable Order Markov Chains for Effective Protection
- Best Practices for Safeguarding APIs from Malicious Activities
- Q&A
- In Retrospect
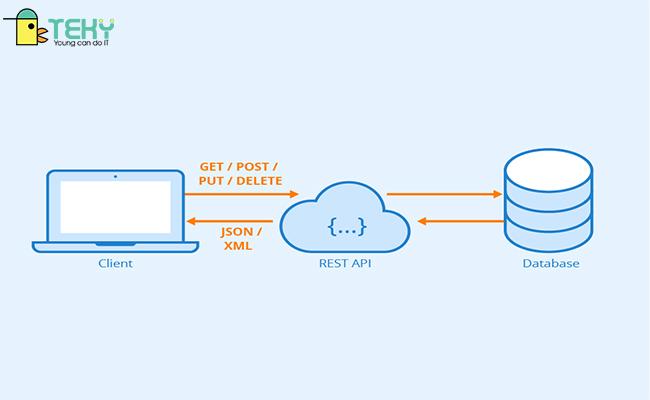
Understanding the Threat of API Abuse
One of the key challenges in today’s digital landscape is protecting APIs from abuse. With the increasing reliance on APIs for communication between different software systems, the risk of malicious attacks and unauthorized access is higher than ever. Traditional security measures are often not enough to prevent API abuse, making it essential for organizations to explore innovative solutions.
One approach to protecting APIs from abuse is using sequence learning and variable order Markov chains. By analyzing the patterns of API calls and responses, organizations can detect anomalous behavior and take proactive measures to prevent potential attacks. This advanced technique allows for real-time monitoring of API activity, helping to identify and mitigate security threats before they escalate. By leveraging the power of sequence learning and Markov chains, organizations can enhance their API security posture and safeguard sensitive data from unauthorized access.
Implementing Sequence Learning for Enhanced Security
By utilizing sequence learning and variable order Markov chains, we can enhance the security of APIs and protect them from potential abuse. These advanced techniques allow us to analyze patterns in API requests and responses, helping us detect and prevent unauthorized access or malicious activities.
The use of machine learning algorithms in conjunction with variable order Markov chains enables us to create robust models that can adapt to evolving security threats. This proactive approach to security not only helps in mitigating risks but also improves the overall reliability and performance of APIs.
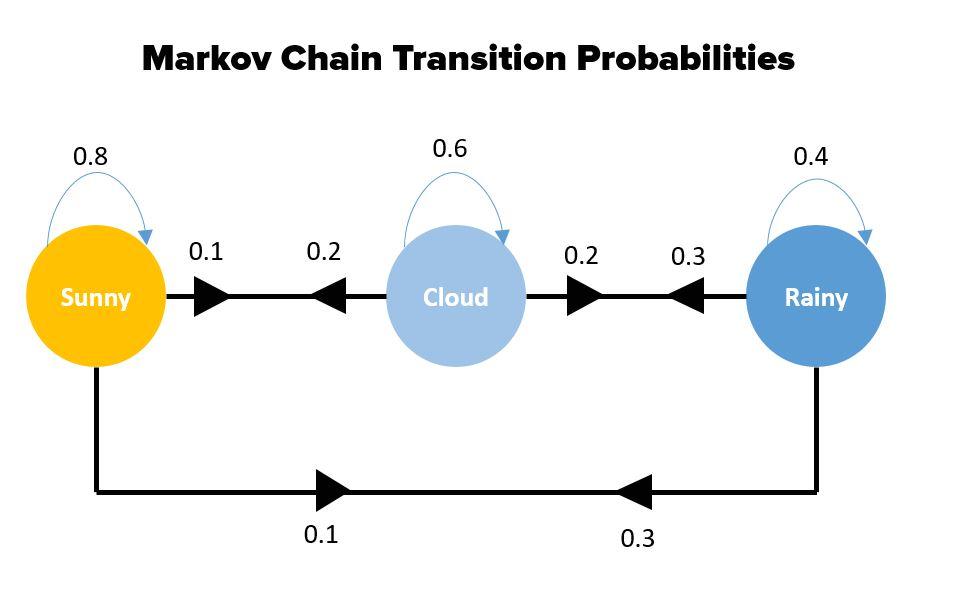
Utilizing Variable Order Markov Chains for Effective Protection
When it comes to protecting APIs from abuse, utilizing sequence learning and variable order Markov chains can be a game-changer. By analyzing the patterns of API requests and responses, we can effectively detect and prevent malicious activities before they cause any harm.
With variable order Markov chains, we can model the sequences of API calls and predict the next request based on the history of interactions. This allows us to proactively block any suspicious activities and ensure the security of our APIs. By combining the power of sequence learning algorithms with advanced statistical models, we can stay one step ahead of potential attackers and keep our systems safe from cyber threats.

Best Practices for Safeguarding APIs from Malicious Activities
One effective way to safeguard APIs from malicious activities is by utilizing sequence learning and variable order Markov chains. By implementing these advanced techniques, developers can better detect and prevent unauthorized access, data breaches, and other security threats.
With sequence learning, the system analyzes the patterns and sequences of API calls to identify potential anomalies or suspicious behavior. Variable order Markov chains, on the other hand, help in predicting the next API call based on historical data, allowing for proactive security measures to be implemented. By combining these two approaches, developers can create a robust defense mechanism against API abuse and ensure the integrity and confidentiality of their systems.
Q&A
Q: What is the primary focus of the article “Protecting APIs from abuse using sequence learning and variable order Markov chains”?
A: The article focuses on utilizing advanced technologies such as sequence learning and variable order Markov chains to safeguard APIs from potential abuse.
Q: How do sequence learning and Markov chains help in protecting APIs?
A: Sequence learning allows for the analysis of patterns in API usage, while variable order Markov chains help in predicting future API calls based on past behavior, enabling proactive protection against abuse.
Q: What are the potential risks of API abuse?
A: API abuse can lead to information leaks, data manipulation, server overload, and unauthorized access to sensitive information, posing a significant threat to security and system integrity.
Q: How does the adoption of these technologies benefit organizations in terms of API security?
A: By leveraging sequence learning and Markov chains, organizations can enhance their API security measures by detecting and preventing abusive behavior in real-time, ultimately reducing the risk of potential attacks and breaches.
Q: Are there any limitations or challenges associated with implementing these advanced techniques?
A: Some challenges may include the need for large datasets for effective sequence learning, as well as resource-intensive computational requirements for building and maintaining Markov chains. However, the long-term benefits of enhanced API security outweigh these challenges.
In Retrospect
protecting APIs from abuse is a crucial task in today’s digital landscape. By utilizing sequence learning and variable order Markov chains, developers can enhance the security of their APIs and mitigate potential attacks. Whether it’s preventing malicious bots from overwhelming servers or safeguarding sensitive user data, incorporating these technologies can help ensure a safe and reliable user experience. Stay vigilant, stay proactive, and together we can continue to safeguard the integrity of our digital ecosystem.











Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere.
Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil.
Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore.