In the vast realm of cloud computing, Kubernetes reigns as the king of container orchestration. However, with great power comes great responsibility. As the heart of your infrastructure, it’s crucial to fortify your Kubernetes cluster against potential threats. In this article, we’ll delve into the world of Kubernetes security and explore essential tips and best practices to ensure the iron-clad protection of your cluster. Join us on this journey to secure your Kubernetes kingdom.
Table of Contents
- Securing Your Kubernetes Cluster: Best Practices for Authentication and Authorization
- Protecting Your Kubernetes Cluster: Network Policies and Pod Security
- Ensuring a Secure Kubernetes Cluster: Monitoring, Logging, and Regular Auditing
- Advanced Techniques for Securing Your Kubernetes Cluster: RBAC and TLS Encryption
- Q&A
- Future Outlook
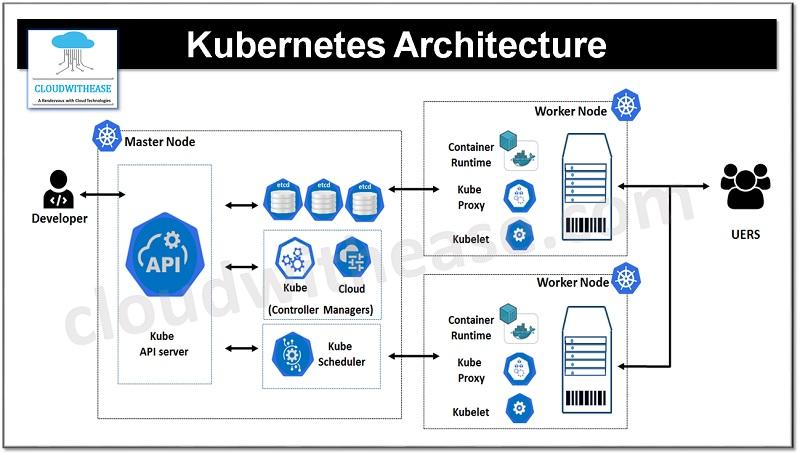
Securing Your Kubernetes Cluster: Best Practices for Authentication and Authorization
Ensuring the security of your Kubernetes cluster is crucial in protecting your applications and data from unauthorized access and potential breaches. By following best practices for authentication and authorization, you can significantly reduce the risk of security issues. One key aspect of securing your Kubernetes cluster is implementing strong authentication mechanisms. This involves properly verifying the identities of users and services attempting to access the cluster.
One effective way to enhance authentication is by implementing multi-factor authentication (MFA) for all users. This adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password and a unique code sent to their mobile device. Additionally, utilizing role-based access control (RBAC) can help in ensuring that only authorized users have access to specific resources within the cluster. By defining roles with specific permissions, you can limit the scope of access for individual users or services, reducing the potential for unauthorized actions.
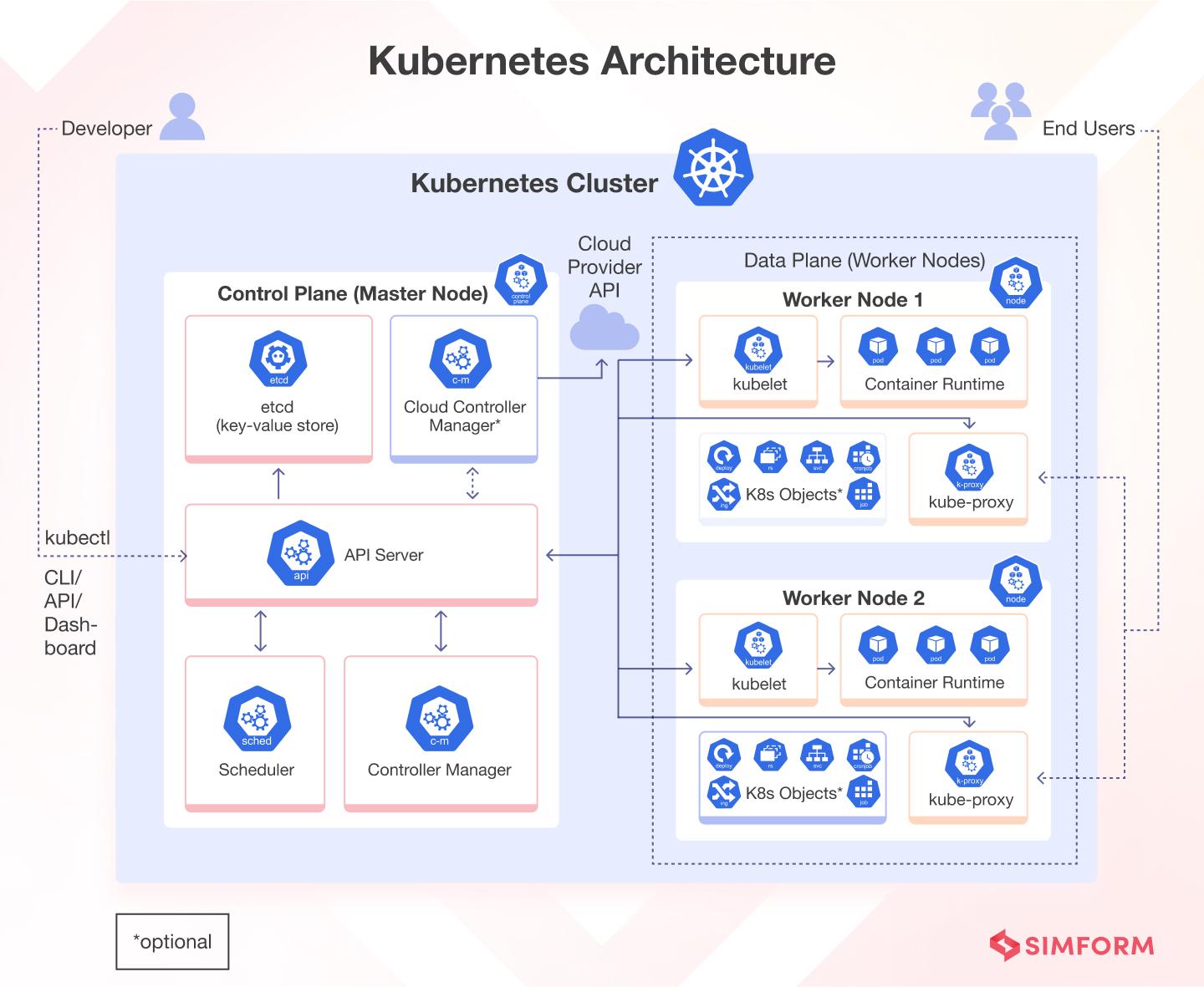
Protecting Your Kubernetes Cluster: Network Policies and Pod Security
When it comes to securing your Kubernetes cluster, implementing network policies and pod security are crucial steps to protect your infrastructure. By defining and enforcing network policies, you can control the flow of traffic within your cluster, ensuring that only authorized communication is allowed. This helps prevent unauthorized access and potential security breaches.
Additionally, enhancing pod security measures such as restricting the use of privileged containers, implementing security context constraints, and utilizing pod security policies can help mitigate risks and vulnerabilities. By following best practices and staying up-to-date on security guidelines, you can strengthen the overall security posture of your Kubernetes cluster and safeguard your critical workloads from potential threats.

Ensuring a Secure Kubernetes Cluster: Monitoring, Logging, and Regular Auditing
When it comes to securing your Kubernetes cluster, monitoring, logging, and regular auditing are key components that cannot be overlooked. By implementing a comprehensive approach that covers all aspects of security, you can help protect your cluster from potential threats and vulnerabilities.
One way to ensure the security of your Kubernetes cluster is by setting up monitoring tools such as Prometheus and Grafana to keep track of system metrics and performance data in real-time. Additionally, implementing centralized logging with tools like ELK Stack can help you quickly identify and respond to any security incidents. Regularly auditing your cluster by reviewing access controls, permissions, and configurations can also help you stay ahead of potential security risks.
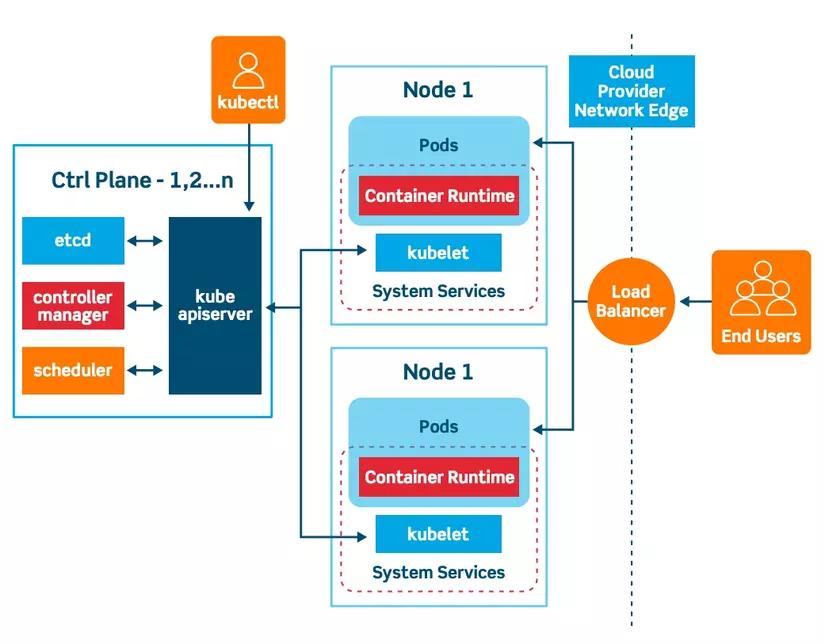
Advanced Techniques for Securing Your Kubernetes Cluster: RBAC and TLS Encryption
In order to ensure the security of your Kubernetes cluster, it is important to utilize advanced techniques such as Role-Based Access Control (RBAC) and Transport Layer Security (TLS) encryption. RBAC allows you to define granular permissions for different users or groups within the cluster, ensuring that only authorized individuals have access to specific resources. This helps to prevent unauthorized access and potential security vulnerabilities.
Additionally, implementing TLS encryption helps to secure communication between components within the cluster. This ensures that data is encrypted in transit, protecting it from potential interception or tampering. By combining RBAC and TLS encryption, you can significantly enhance the security of your Kubernetes cluster and reduce the risk of potential security threats.
Q&A
Q: Why is it important to secure your Kubernetes cluster?
A: Securing your Kubernetes cluster is crucial to protect sensitive data and prevent unauthorized access.
Q: What are some common security risks associated with Kubernetes clusters?
A: Common security risks include misconfigured permissions, insecure container images, and vulnerabilities in Kubernetes components.
Q: How can I improve the security of my Kubernetes cluster?
A: You can improve security by enabling network policies, restricting access to the Kubernetes API, and regularly updating your cluster and applications.
Q: What role does authentication and authorization play in Kubernetes security?
A: Authentication and authorization help ensure that only authorized users and applications can access and manipulate resources within the Kubernetes cluster.
Q: How can I monitor and detect security incidents in my Kubernetes cluster?
A: You can monitor for potential security incidents by using tools such as Kubernetes-native monitoring solutions and implementing logging and auditing practices.
Q: What should I do in case of a security breach in my Kubernetes cluster?
A: In case of a security breach, isolate the affected components, investigate the root cause, and implement measures to prevent future incidents.
Future Outlook
securing your Kubernetes cluster is essential in ensuring the protection and integrity of your data and applications. By incorporating the best practices outlined in this article, you can enhance the security posture of your environment and mitigate potential risks. Remember, a proactive approach to security is key in today’s rapidly evolving threat landscape. So, stay vigilant, stay informed, and stay secure. Happy clustering!










