In the ever-evolving landscape of cyber threats, the need for comprehensive intelligence gathering has become paramount for organizations looking to stay one step ahead of potential security breaches. As part of a proactive approach to cybersecurity, threat intelligence teams are turning to Requests for Information (RFIs) and Priority Intelligence Requirements (PIRs) as invaluable tools in their arsenal. Let’s delve into how these frameworks are being utilized to enhance the capabilities of threat intelligence teams and bolster their defenses against looming threats.
Table of Contents
- Introducing Requests for Information (RFIs) for Efficient Data Collection
- Understanding the Significance of Priority Intelligence Requirements (PIRs)
- Implementing RFIs to Enhance Threat Intelligence Gathering
- Best Practices for Leveraging PIRs in Threat Intelligence Operations
- Q&A
- In Retrospect

Introducing Requests for Information (RFIs) for Efficient Data Collection
RFIs are a valuable tool for threat intelligence teams looking to efficiently gather data for analysis. By leveraging RFIs, teams can request specific information from internal and external sources, streamlining the data collection process and ensuring that only relevant data is gathered. This targeted approach not only saves time and resources but also enhances the quality of the intelligence gathered.
Additionally, PIRs provide threat intelligence teams with a framework for prioritizing their data collection efforts. By establishing clear priorities based on operational needs, teams can focus on gathering the most critical information first, ensuring that decision-makers receive timely and actionable intelligence. This strategic approach to data collection enables teams to stay ahead of emerging threats and respond effectively to evolving security challenges.
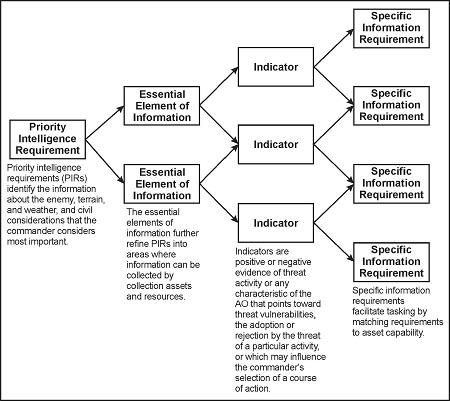
Understanding the Significance of Priority Intelligence Requirements (PIRs)
Priority Intelligence Requirements (PIRs) play a crucial role in the success of threat intelligence teams by guiding them on what specific information to focus on and prioritize. These requirements are essential in ensuring that the team’s efforts are aligned with the organization’s strategic objectives and security needs. By understanding the significance of PIRs, teams can effectively gather, analyze, and disseminate intelligence that is timely, relevant, and actionable.
Requests for Information (RFIs) are a valuable tool that helps threat intelligence teams gather the necessary information to address PIRs effectively. RFIs allow teams to request specific intelligence from various sources, such as internal and external stakeholders, to fill gaps in their knowledge and understanding of potential threats. By leveraging RFIs alongside PIRs, teams can enhance their intelligence collection and analysis capabilities, ultimately leading to more informed decision-making and proactive threat mitigation strategies.

Implementing RFIs to Enhance Threat Intelligence Gathering
Threat intelligence teams play a crucial role in identifying and mitigating potential risks to an organization’s security. By implementing Requests for Information (RFIs) and Priority Intelligence Requirements (PIRs), these teams can enhance their capabilities to gather relevant threat intelligence. RFIs allow teams to request specific information from a variety of sources, while PIRs prioritize the intelligence needs based on the organization’s security goals.
Utilizing RFIs enables threat intelligence teams to fill gaps in their knowledge by requesting targeted information on emerging threats, vulnerabilities, or malicious actors. By setting clear PIRs, teams can focus their efforts on gathering intelligence that directly impacts their organization’s security posture. This structured approach to intelligence gathering ensures that teams are equipped with the necessary information to proactively defend against potential threats.

Best Practices for Leveraging PIRs in Threat Intelligence Operations
When it comes to threat intelligence operations, leveraging Requests for Information (RFIs) and Priority Intelligence Requirements (PIRs) is crucial for success. RFIs allow teams to gather specific information needed to enhance their situational awareness and make informed decisions. By submitting RFIs, analysts can request data on potential threats, vulnerabilities, or adversaries, enabling them to stay ahead of evolving cyber risks.
On the other hand, PIRs help prioritize intelligence collection efforts by identifying the most critical information needed to support the organization’s mission and objectives. Establishing clear PIRs ensures that resources are allocated effectively and that intelligence analysis is focused on addressing key security concerns. By incorporating both RFIs and PIRs into their workflow, threat intelligence teams can streamline their operations and enhance their ability to proactively defend against emerging threats.
Q&A
Q: What are Requests for Information (RFIs) and Priority Intelligence Requirements (PIRs) in the context of threat intelligence teams?
A: RFIs are formal requests made by individuals or teams within an organization seeking specific information related to potential threats or vulnerabilities. PIRs are top-priority information needs identified by leadership that require immediate attention from the threat intelligence team.
Q: How can RFIs and PIRs benefit threat intelligence teams?
A: RFIs and PIRs help streamline the information collection process, prioritize tasks, and ensure that the team is focusing on the most critical issues facing the organization.
Q: How should threat intelligence teams go about creating and managing RFIs and PIRs?
A: Teams should establish clear guidelines for submitting RFIs, prioritize PIRs based on the organization’s strategic goals, and regularly review and update both lists to ensure they remain relevant and effective.
Q: Are there any potential challenges associated with implementing RFIs and PIRs?
A: Some challenges may include determining the appropriate level of detail required for RFIs, managing competing priorities when addressing multiple PIRs, and ensuring that all team members understand the importance of responding to these requests in a timely manner.
Q: How can organizations measure the success of their RFIs and PIRs processes?
A: Organizations can track key metrics such as response time to RFIs, the number of PIRs successfully addressed, and the impact of threat intelligence insights on overall security posture to evaluate the effectiveness of their processes.
In Retrospect
implementing Requests for Information (RFIs) and Priority Intelligence Requirements (PIRs) within your threat intelligence team can greatly enhance your organization’s ability to identify and mitigate potential threats. By leveraging these tools effectively, you can stay one step ahead of adversaries and safeguard your critical assets. Remember, a proactive approach to threat intelligence is key in today’s ever-evolving digital landscape. Stay informed, stay prepared, and stay safe. Thank you for reading.










