As technology continues to advance at an unprecedented rate, the importance of securing our systems and data has never been more critical. One vital aspect of this security strategy is ensuring the protection of the Linux kernel, the core component of the open-source operating system. In this article, we explore essential security tunables that everyone should consider adopting to fortify their Linux system against potential threats. Whether you’re a seasoned Linux user or a newcomer to the platform, implementing these tunables can significantly enhance the security of your system and protect it from malicious attacks.
Table of Contents
- Header Guard Protection for Kernel Code
- Proactive Auditing Tools to Enhance Security
- Implementing Secure Compilers for Linux Kernel
- Enhancing Kernel Security with Virtualization Techniques
- Q&A
- Future Outlook

Header Guard Protection for Kernel Code
When it comes to securing the Linux kernel, one important aspect to consider is implementing . By utilizing header guards, developers can prevent header files from being included multiple times in the same compilation unit, thus avoiding issues such as redefinition errors and conflicts.
One simple way to enable header guard protection is by including conditional statements in header files to check if a particular macro has already been defined. If not, the header file contents are processed, and the macro is defined to prevent further inclusion. This helps ensure that each header file is included only once, maintaining code integrity and preventing unexpected behavior.

Proactive Auditing Tools to Enhance Security
One of the most important aspects of enhancing security on a Linux system is to utilize proactive auditing tools that can help identify potential vulnerabilities before they can be exploited. By implementing these tools, system administrators can stay one step ahead of potential attackers and ensure that their systems are as secure as possible.
Some key Linux kernel security tunables that everyone should consider adopting include:
- SELinux (Security-Enhanced Linux): This security module provides a flexible and fine-grained Mandatory Access Control (MAC) system. By enforcing security policies at the kernel level, SELinux can prevent unauthorized access and protect sensitive data.
- GRSecurity: This patch for the Linux kernel includes a variety of security enhancements, such as Role-Based Access Control (RBAC), Address Space Layout Randomization (ASLR), and more. These features can help mitigate common security threats and protect against privilege escalation attacks.
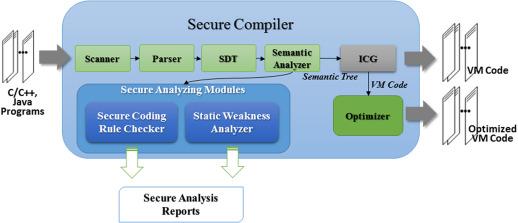
Implementing Secure Compilers for Linux Kernel
One crucial aspect of enhancing the security of the Linux kernel is by implementing secure compilers. By utilizing tools that prioritize security during the compilation process, developers can reduce the risk of vulnerabilities being introduced into the kernel code. Secure compilers help enforce strict coding standards and best practices, ultimately leading to a more secure and robust kernel.
Some key security tunables that every Linux user should consider adopting include:
- Position-Independent Executable (PIE) Support: Enabling PIE support can help prevent certain types of attacks, such as code injection, by randomizing memory address space.
- Control Flow Integrity (CFI): Implementing CFI can help protect against control-flow hijacking attacks by validating the integrity of function call targets.
- Stack Protector: Enabling stack protector can provide an additional layer of security by detecting and preventing stack buffer overflow vulnerabilities.

Enhancing Kernel Security with Virtualization Techniques
Virtualization techniques offer a powerful way to enhance the security of the Linux kernel by isolating different processes and workloads. By utilizing tools such as containers and hypervisors, organizations can create separate environments for applications, reducing the attack surface and the risk of security breaches.
Some key kernel security tunables that everyone should consider adopting include:
- SELinux (Security-Enhanced Linux): Enforcing mandatory access controls to limit the actions that processes can take.
- Grsecurity: Providing enhanced security features such as role-based access control and restrictions on kernel vulnerabilities.
- AppArmor: Controlling access to specific applications by enforcing security policies.
Q&A
Q: What are Linux kernel security tunables?
A: Linux kernel security tunables are settings that can be adjusted in the Linux kernel to enhance system security and protect against potential threats.
Q: Why should I consider adopting these tunables?
A: By adopting these tunables, you can strengthen the security of your system and reduce the risk of malicious attacks or breaches.
Q: What are some examples of security tunables that I should consider implementing?
A: Some examples of security tunables include enabling address space layout randomization (ASLR), implementing strict memory protections, and configuring firewall rules.
Q: How do I go about adjusting these tunables in the Linux kernel?
A: You can adjust these security tunables by modifying kernel parameters in the system configuration files or using security-focused tools and software.
Q: Are there any potential drawbacks to implementing these tunables?
A: While implementing these tunables can enhance security, it’s important to consider potential compatibility issues with certain applications or services that may be affected by the changes.
Q: What steps should I take before implementing these tunables to ensure a smooth transition?
A: Before implementing these tunables, it’s recommended to thoroughly research and understand each setting, perform thorough testing in a controlled environment, and create backups to mitigate any potential risks.
Future Outlook
by implementing these Linux kernel security tunables, you can strengthen the security of your system and protect it from potential threats. Remember that each tunable comes with its own set of benefits and trade-offs, so make sure to carefully consider which ones are most suitable for your specific needs. By taking proactive measures to secure your Linux kernel, you can ensure that your data and system remain safe and reliable. So don’t wait any longer – start implementing these tunables today and fortify your defenses against cyber attacks. Stay safe, stay secure, and happy computing!