Bigger and badder: how DDoS attack sizes have evolved over the last decade
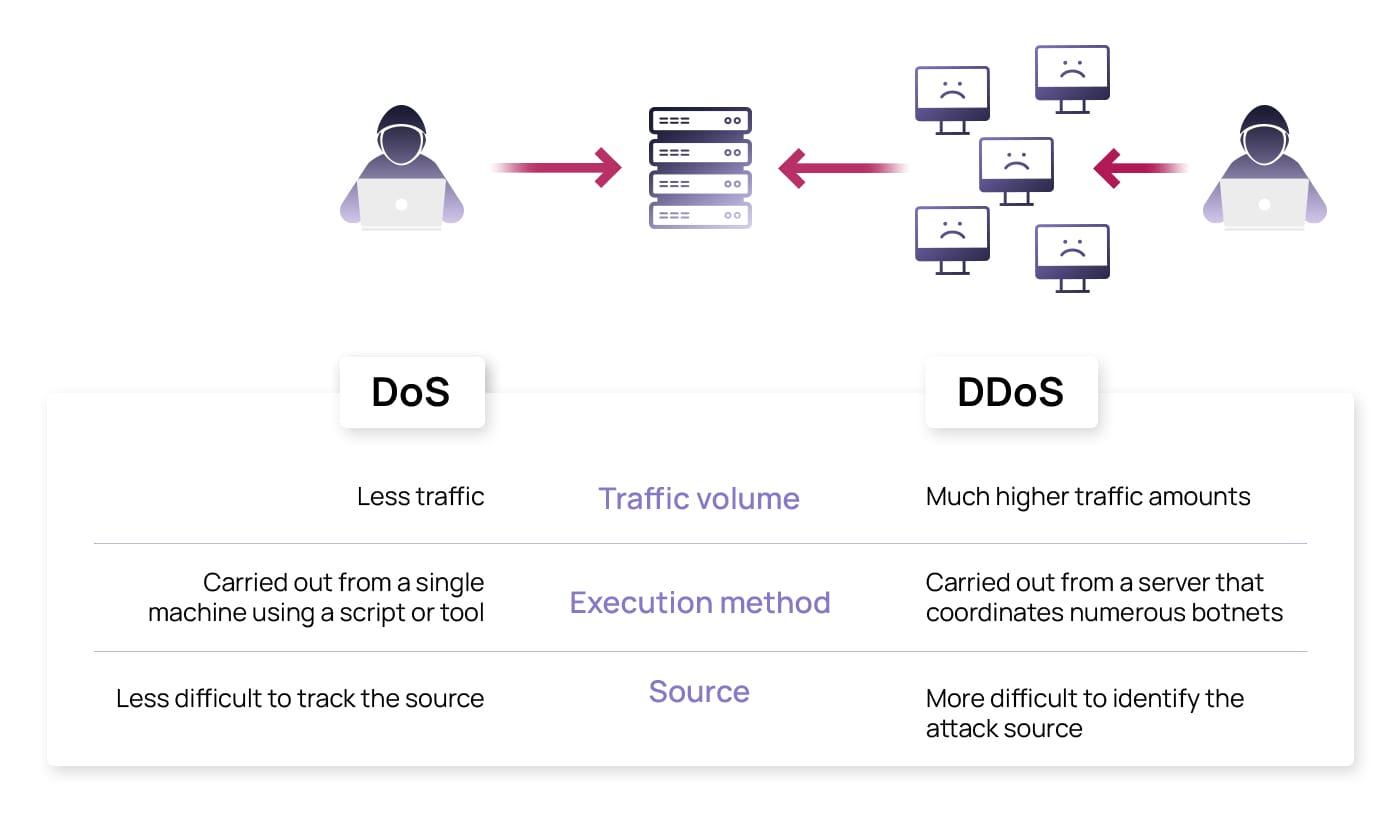
Over the past decade, Distributed Denial of Service (DDoS) attacks have grown in size and complexity, making them harder to defend against. From simple attacks targeting websites to sophisticated assaults on entire networks, the evolution of DDoS attacks poses a significant challenge to cybersecurity experts.
Read more
What’s new in Cloudflare: Account Owned Tokens and Zaraz Automated Actions

Discover the latest enhancements in Cloudflare with the introduction of Account Owned Tokens and Zaraz Automated Actions. These new features promise to streamline security and performance for users.
Read more
Protect against identity-based attacks by sharing Cloudflare user risk scores with Okta

Cloudflare and Okta team up to boost security measures against identity-based attacks. By sharing user risk scores, businesses can stay one step ahead of potential threats. Stay protected in the cloud with this powerful partnership.
Read more
Avoiding downtime: modern alternatives to outdated certificate pinning practices

Downtime is a nightmare for businesses, but traditional certificate pinning practices can cause more harm than good. Learn about modern alternatives to keep your systems secure and running smoothly.
Read more
Protecting APIs from abuse using sequence learning and variable order Markov chains

In a world where API abuse is rampant, businesses are turning to innovative solutions like sequence learning and variable order Markov chains to protect their valuable data. These cutting-edge techniques are revolutionizing the way we safeguard APIs.
Read more
Introducing Ephemeral IDs: a new tool for fraud detection
Introducing Ephemeral IDs: the innovative new tool that is revolutionizing fraud detection. Say goodbye to traditional methods and hello to enhanced security with this cutting-edge technology.
Read more
Continuing our work with CISA and the Joint Cyber Defense Collaborative to keep vulnerable communities secure online

As we move forward in our partnership with CISA and the Joint Cyber Defense Collaborative, we remain committed to protecting vulnerable communities online. Stay tuned to see how we are working together to enhance cybersecurity measures for those who need it most.
Read more
Introducing Automatic SSL/TLS: securing and simplifying origin connectivity
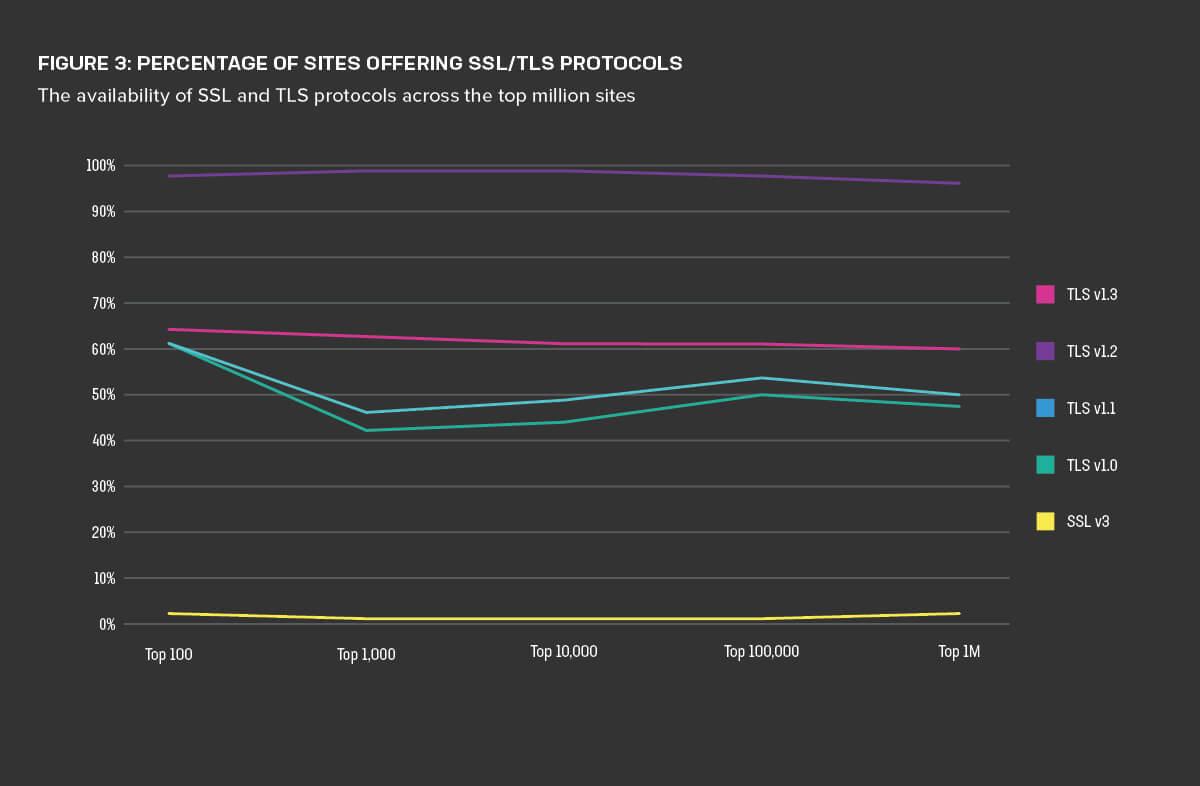
In the ever-evolving landscape of cybersecurity, the introduction of Automatic SSL/TLS is revolutionizing the way we secure and simplify origin connectivity. With this game-changing technology, organizations can rest assured that their data is protected without the hassle of manual configurations.
Read more









