Cloudflare 2024 Year in Review

Step into the future with Cloudflare's 2024 Year in Review. Explore the highlights of the past year in cybersecurity, network performance, and more.
Read more
Bigger and badder: how DDoS attack sizes have evolved over the last decade
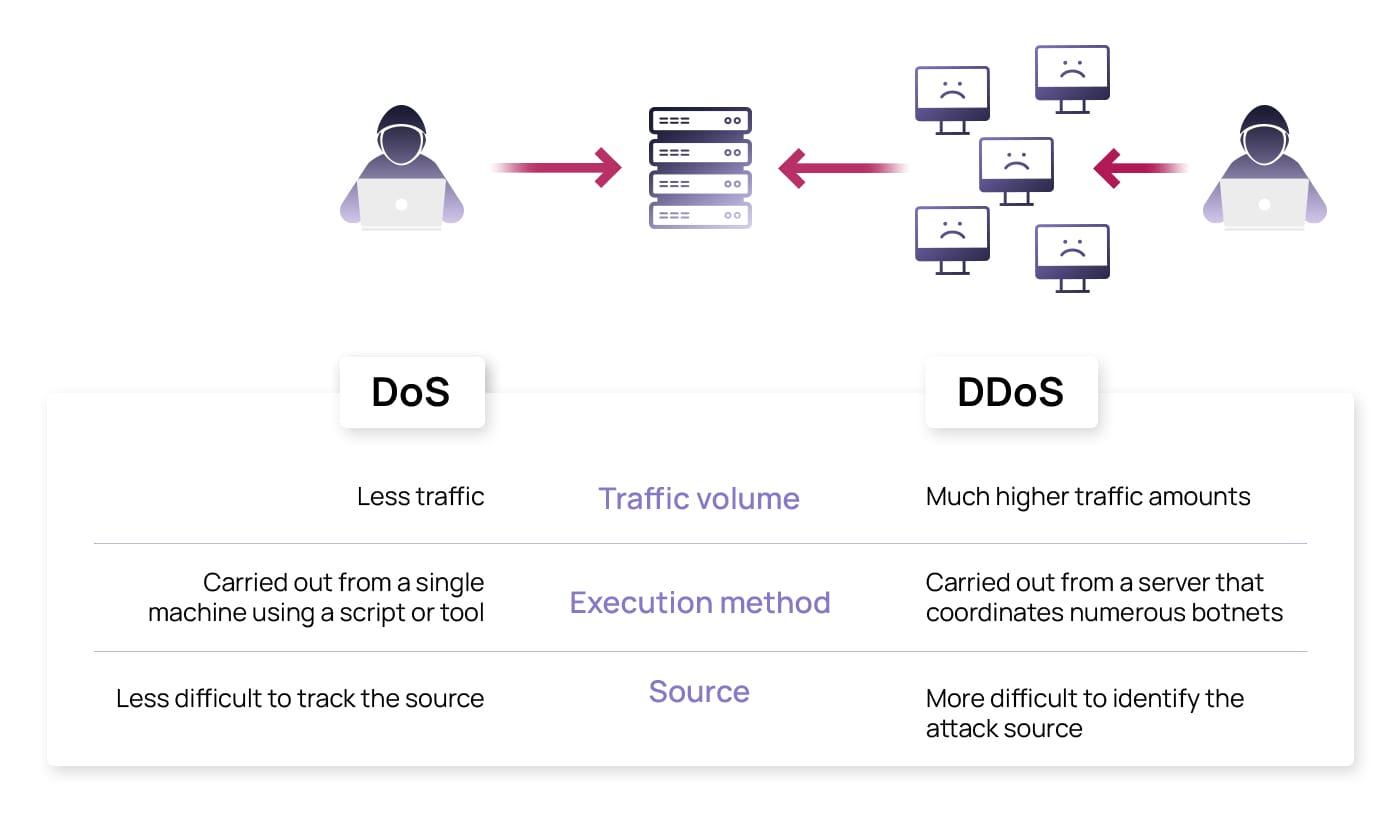
Over the past decade, Distributed Denial of Service (DDoS) attacks have grown in size and complexity, making them harder to defend against. From simple attacks targeting websites to sophisticated assaults on entire networks, the evolution of DDoS attacks poses a significant challenge to cybersecurity experts.
Read more
Exploring Internet traffic shifts and cyber attacks during the 2024 US election
In the digital battleground of the 2024 US election, internet traffic shifts and cyber attacks played a pivotal role. Understanding these trends is crucial in safeguarding the integrity of future elections.
Read more
Introducing Access for Infrastructure: SSH
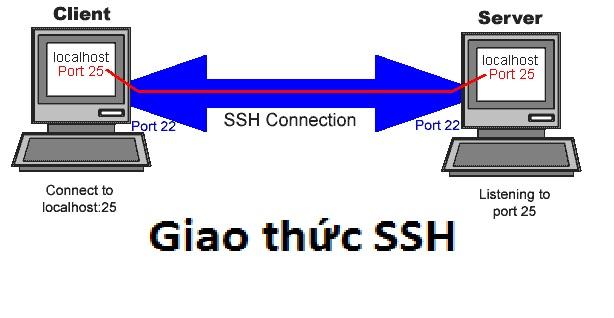
Access for Infrastructure simplifies remote server management with SSH. It provides secure access to servers, ensuring efficient deployment and maintenance.
Read more
What’s new in Cloudflare One: Digital Experience (DEX) monitoring notifications and seamless access to Cloudflare Gateway with China Express

Explore the latest features in Cloudflare One, including Digital Experience monitoring notifications and seamless access to Cloudflare Gateway with China Express. Stay ahead of the game with these cutting-edge updates.
Read more
Cloudflare acquires BastionZero to extend Zero Trust access to IT infrastructure

In a strategic move to enhance their security offerings, Cloudflare has acquired BastionZero to further expand Zero Trust access to IT infrastructure. This collaboration is set to revolutionize the cybersecurity landscape.
Read more
Enhancing security analysis with Cloudflare Zero Trust logs and Elastic SIEM

By integrating Cloudflare Zero Trust logs with Elastic SIEM, security analysts can gain deeper insights into their network activity and potential threats. This powerful combination enhances overall security posture and threat detection capabilities.
Read more
A global assessment of third-party connection tampering

In a world where interconnectivity is key, a global assessment of third-party connection tampering has revealed alarming vulnerabilities. From data breaches to unauthorized access, the risk posed by these malicious interlopers is a growing concern for businesses and individuals alike.
Read more
How to Spot and Stop a DDoS Attack

As the digital landscape continues to evolve, DDoS attacks have become more prevalent. Learn how to recognize the signs and take action against these malicious threats before they disrupt your online presence.
Read more
What Is TCP DDoS Protection? | How Does It Work?

TCP DDoS protection is a crucial defense mechanism against harmful cyber attacks. By monitoring and filtering incoming traffic, it safeguards the network from overwhelming malicious requests. Let's delve into the intricacies of how this technology operates to keep our data safe.
Read more









