In the ever-evolving landscape of cyber threats, Distributed Denial of Service (DDoS) attacks have continued to grow in both size and complexity over the past decade. These malicious attacks, once a mere inconvenience for website owners, have transformed into formidable weapons capable of crippling even the most robust online platforms. Join us as we explore the evolution of DDoS attack sizes and the implications for the future of cybersecurity.
Table of Contents
- A Decade of Evolution: Tracking the Growth of DDoS Attack Sizes
- Impact on Businesses: How Larger DDoS Attacks Are Testing Cyber Defenses
- Mitigation Strategies: Strengthening Your Defense Against Massive DDoS Attacks
- Looking Ahead: Preparing for the Future of DDoS Threats
- Q&A
- The Conclusion

A Decade of Evolution: Tracking the Growth of DDoS Attack Sizes
Over the past ten years, the landscape of DDoS attacks has undergone a significant transformation, with attackers constantly finding new ways to amplify the size and impact of their assaults. From the humble beginnings of small-scale attacks targeting individual websites, we have witnessed a meteoric rise in the scale and complexity of these attacks, capable of taking down entire networks and services. The evolution of DDoS attack sizes has been nothing short of exponential, posing a growing challenge for businesses and organizations worldwide.
One key trend in the evolution of DDoS attacks has been the increasing use of sophisticated techniques such as botnets, amplification attacks, and IoT devices to launch massive distributed denial of service assaults. Attackers are leveraging these methods to generate unprecedented volumes of malicious traffic, overwhelming even the most robust defense mechanisms. As a result, the average size of DDoS attacks has grown dramatically over the past decade, making it imperative for cybersecurity professionals to stay vigilant and continually adapt their strategies to mitigate the ever-growing threat landscape.

Impact on Businesses: How Larger DDoS Attacks Are Testing Cyber Defenses
As DDoS attacks continue to grow in size and complexity, businesses are facing unprecedented challenges in defending against these malicious threats. Larger DDoS attacks are now testing the cyber defenses of even the most well-prepared organizations, pushing them to reevaluate their security strategies and invest in more robust solutions. In recent years, the average size of DDoS attacks has increased significantly, with some attacks exceeding 1 terabit per second in bandwidth.
This escalation in attack size is forcing businesses to rethink their approach to cybersecurity, emphasizing the importance of proactive defense measures and real-time threat detection. As attackers become more sophisticated and resourceful, organizations must stay one step ahead by implementing advanced mitigation techniques and leveraging machine learning algorithms to identify and neutralize DDoS threats quickly. In this evolving landscape of cyber warfare, businesses must prioritize resilience and agility to withstand the impact of larger DDoS attacks and maintain operational continuity.
Mitigation Strategies: Strengthening Your Defense Against Massive DDoS Attacks
As the digital landscape continues to evolve, so too do the tactics of malicious actors looking to disrupt online services. Over the past decade, Distributed Denial of Service (DDoS) attacks have grown exponentially in size and complexity, posing a significant threat to organizations of all sizes. These attacks, which flood a target website or server with massive amounts of traffic, can overwhelm even the most robust defense mechanisms, leading to downtime, data breaches, and significant financial losses.
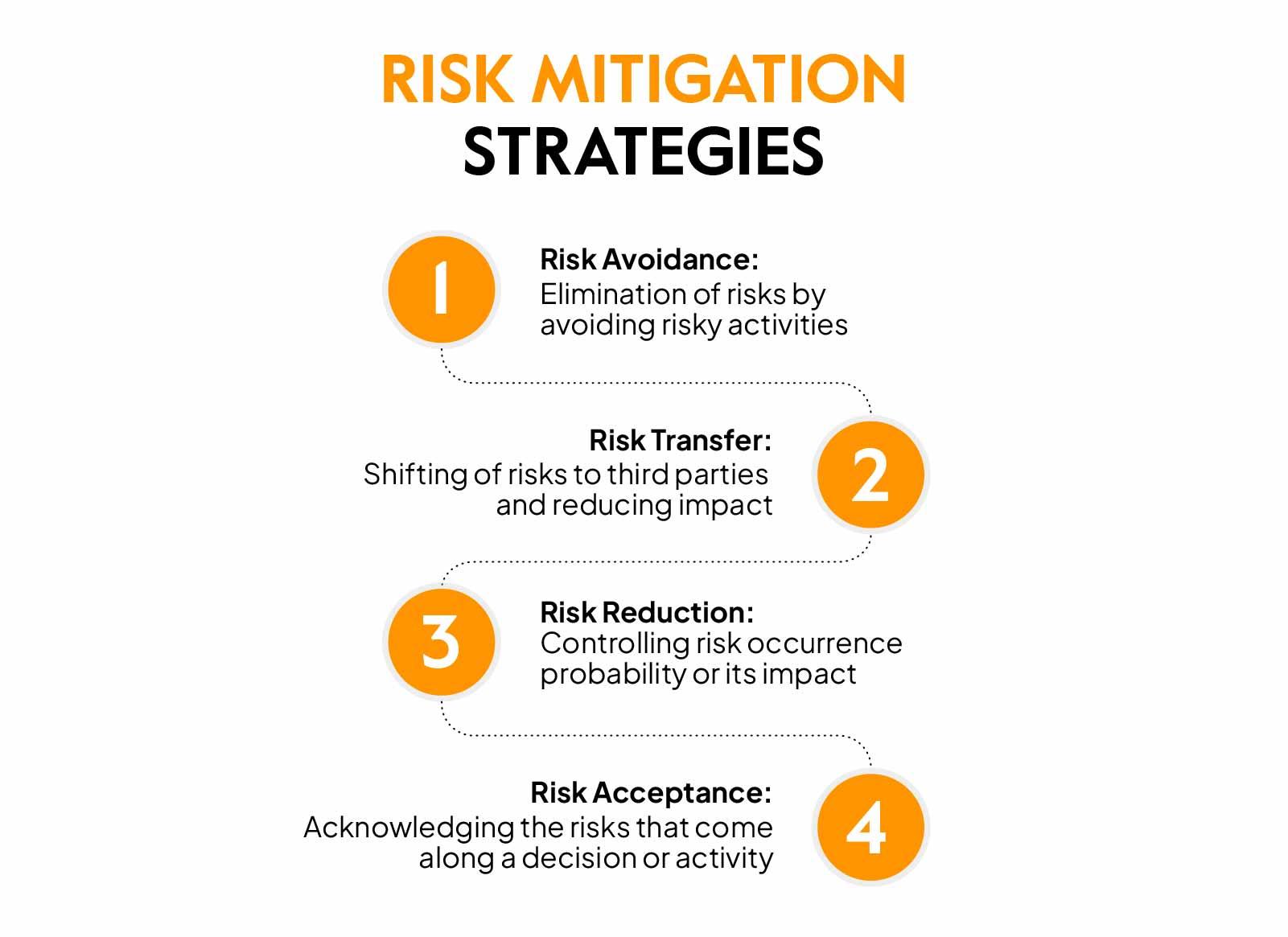
To combat the increasing size and sophistication of DDoS attacks, organizations must implement comprehensive mitigation strategies to strengthen their defenses. From investing in dedicated DDoS protection services to leveraging the latest in network security technologies, there are a variety of countermeasures that can help organizations mitigate the impact of these attacks. By staying vigilant, proactive, and adaptive in their approach to cybersecurity, organizations can better protect their critical assets and maintain a strong defense against the ever-evolving threat of massive DDoS attacks.
Looking Ahead: Preparing for the Future of DDoS Threats
Over the last decade, DDoS attack sizes have seen a significant increase, with attackers constantly finding new ways to amplify their capabilities. What used to be considered a large attack ten years ago would now be considered a mere drop in the bucket compared to the massive assaults we see today. This evolution in size and scale has made it crucial for organizations to stay ahead of the curve and continuously adapt their defense strategies.
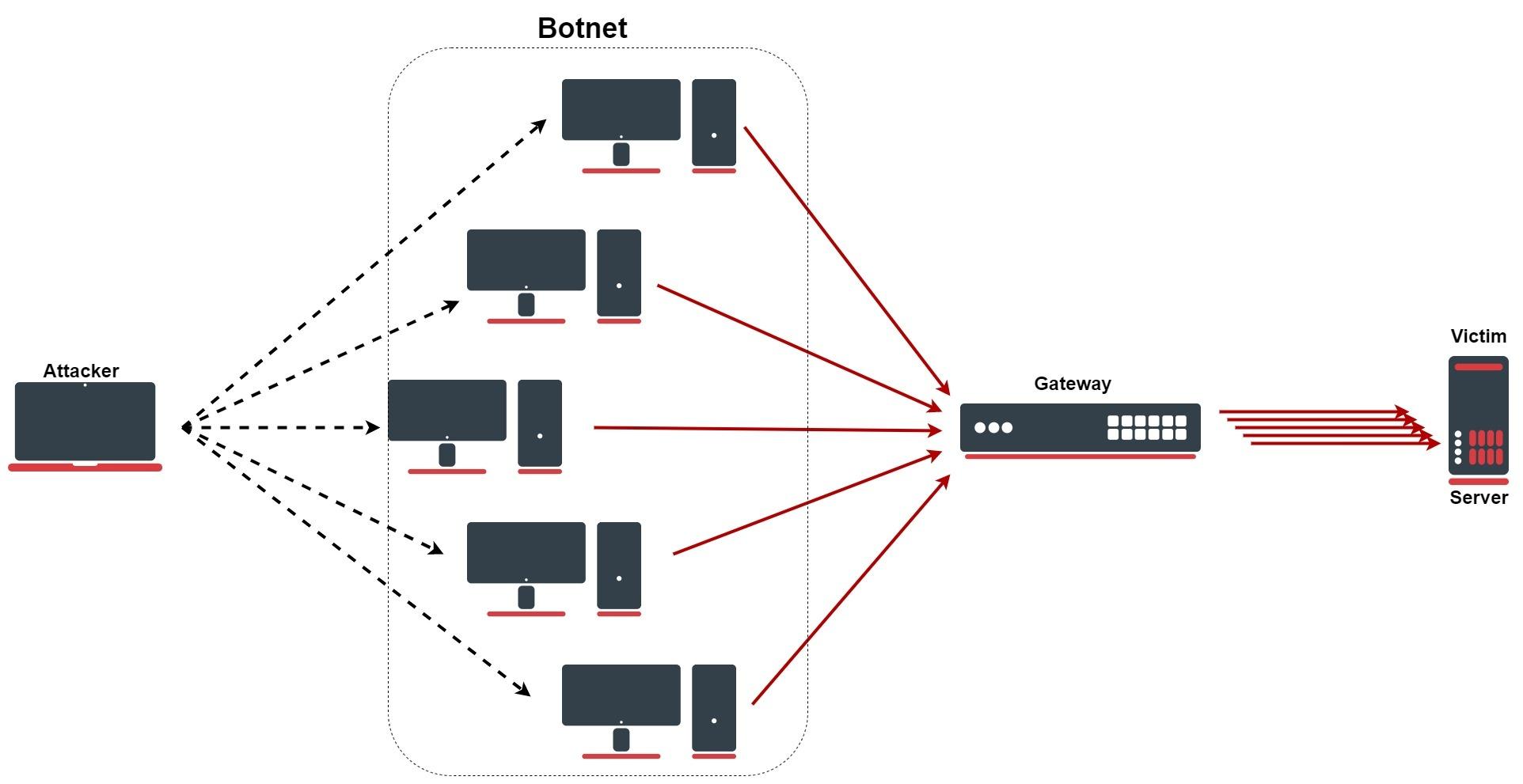
One of the key factors driving the increase in DDoS attack sizes is the proliferation of Internet of Things (IoT) devices. These interconnected devices provide attackers with a vast array of potential targets to exploit, allowing them to build botnets capable of generating massive amounts of traffic. In addition, advancements in technology have enabled attackers to launch more sophisticated and powerful attacks, making it more challenging for businesses to mitigate the impact. To effectively combat these evolving threats, organizations must invest in robust DDoS protection solutions that can detect and block attacks in real-time, ensuring the security and availability of their online assets.
Q&A
Q: What is a DDoS attack?
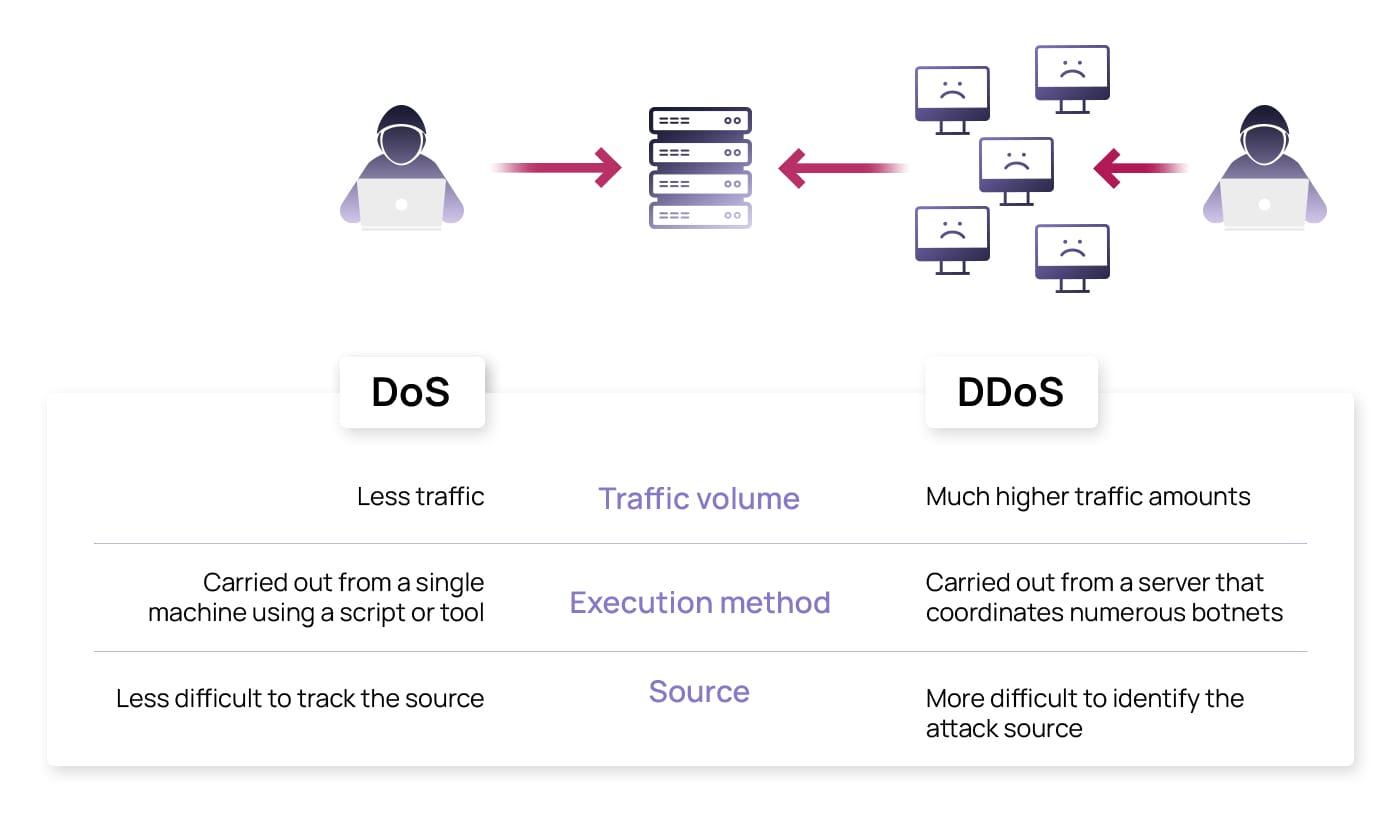
A: A DDoS (Distributed Denial of Service) attack is a malicious attempt to disrupt normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic.
Q: How have DDoS attack sizes evolved over the last decade?
A: Over the past decade, DDoS attack sizes have grown significantly in size and complexity. Attackers are now able to generate larger volumes of traffic, making it more challenging for organizations to defend against such attacks.
Q: What are some of the tactics used by attackers to amplify the size of DDoS attacks?
A: Attackers often utilize tactics such as botnets, amplification techniques (such as DNS amplification), and reflection attacks to amplify the size of DDoS attacks and maximize their impact.
Q: How have organizations adapted to defend against these increasingly large DDoS attacks?
A: Organizations have implemented various DDoS mitigation strategies, including the use of dedicated DDoS protection services, increasing network capacity, and employing advanced threat detection and response technologies to help mitigate the impact of these attacks.
Q: What are some of the potential consequences of a successful DDoS attack on an organization?
A: The consequences of a successful DDoS attack can range from downtime and financial losses to reputational damage and loss of customer trust. Organizations may also face regulatory fines and legal repercussions if they fail to adequately protect against DDoS attacks.
The Conclusion
As technology continues to advance, so too do the tactics used by cybercriminals to launch devastating DDoS attacks. The evolution of attack sizes over the past decade serves as a stark reminder of the constant battle between those seeking to protect and those seeking to disrupt. By staying vigilant and implementing robust cybersecurity measures, we can hope to mitigate the impact of these evolving threats. Stay safe, stay informed, and stay one step ahead in the ever-changing landscape of cyber warfare.