Cloudflare helps verify the security of end-to-end encrypted messages by auditing key transparency for WhatsApp

Cloudflare's innovative technology now plays a crucial role in ensuring the security of end-to-end encrypted messages on WhatsApp through key transparency auditing. This advancement strengthens the privacy and trust of users worldwide.
Read more
Avoiding downtime: modern alternatives to outdated certificate pinning practices

Downtime is a nightmare for businesses, but traditional certificate pinning practices can cause more harm than good. Learn about modern alternatives to keep your systems secure and running smoothly.
Read more
A safer Internet with Cloudflare: free threat intelligence, analytics, and new threat detections

Unleash the power of Cloudflare and protect your online presence with free threat intelligence, advanced analytics, and cutting-edge threat detections. Stay one step ahead of cyber threats and create a safer Internet for all.
Read more
Cloudflare announces Firewall for AI

Cloudflare's latest innovation blends the power of AI with their renowned security features. The new Firewall for AI promises to revolutionize online protection.
Read more
Cloudflare acquires BastionZero to extend Zero Trust access to IT infrastructure

In a strategic move to enhance their security offerings, Cloudflare has acquired BastionZero to further expand Zero Trust access to IT infrastructure. This collaboration is set to revolutionize the cybersecurity landscape.
Read more
Enhancing security analysis with Cloudflare Zero Trust logs and Elastic SIEM

By integrating Cloudflare Zero Trust logs with Elastic SIEM, security analysts can gain deeper insights into their network activity and potential threats. This powerful combination enhances overall security posture and threat detection capabilities.
Read more
Safeguarding your brand identity: Logo Matching for Brand Protection

Logo matching is essential for brand protection. Safeguard your brand identity by monitoring and enforcing the use of your logo to maintain brand consistency.
Read more
Helping keep customers safe with leaked password notification
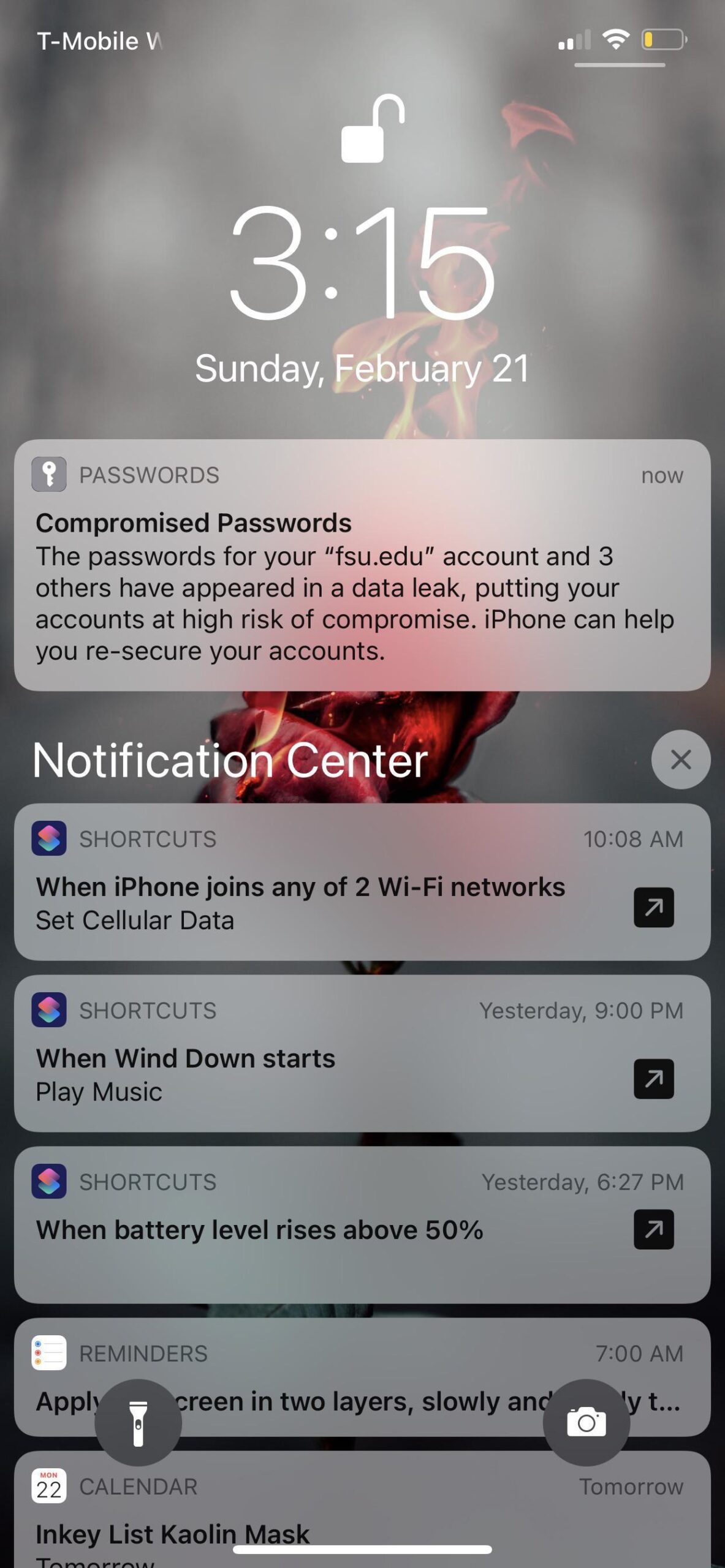
In a world where cyber threats are constantly evolving, leaked password notifications are a crucial tool in protecting customers. By promptly alerting individuals to compromised passwords, businesses can help prevent unauthorized access to personal accounts and data.
Read more
How we ensure Cloudflare customers aren’t affected by Let’s Encrypt’s certificate chain change

In a seamless transition, Cloudflare is working around the clock to ensure customers are shielded from any disruptions caused by Let's Encrypt's certificate chain change. Find out how we are keeping your online presence secure and uninterrupted.
Read more