Continuing our work with CISA and the Joint Cyber Defense Collaborative to keep vulnerable communities secure online

As we move forward in our partnership with CISA and the Joint Cyber Defense Collaborative, we remain committed to protecting vulnerable communities online. Stay tuned to see how we are working together to enhance cybersecurity measures for those who need it most.
Read more
Log Explorer: monitor security events without third-party storage

Introducing Log Explorer - the ultimate tool for monitoring security events without the need for third-party storage. Keep your data safe and secure with this innovative solution.
Read more
Secure your unprotected assets with Security Center: quick view for CISOs
Unleash the power of Security Center to safeguard your organization's most vulnerable assets. CISOs, gain a quick overview of your protection measures and take control of your security strategy with ease.
Read more
Upcoming Let’s Encrypt certificate chain change and impact for Cloudflare customers

Get ready for a change in Let's Encrypt certificates, affecting Cloudflare customers. Stay informed to ensure seamless security for your website.
Read more
Introducing Requests for Information (RFIs) and Priority Intelligence Requirements (PIRs) for threat intelligence teams

Introducing RFIs and PIRs offers threat intelligence teams a structured approach to gathering crucial information. These tools enhance efficiency and focus in identifying and mitigating threats.
Read more
10 Common Web Performance Mistakes and How to Overcome Them
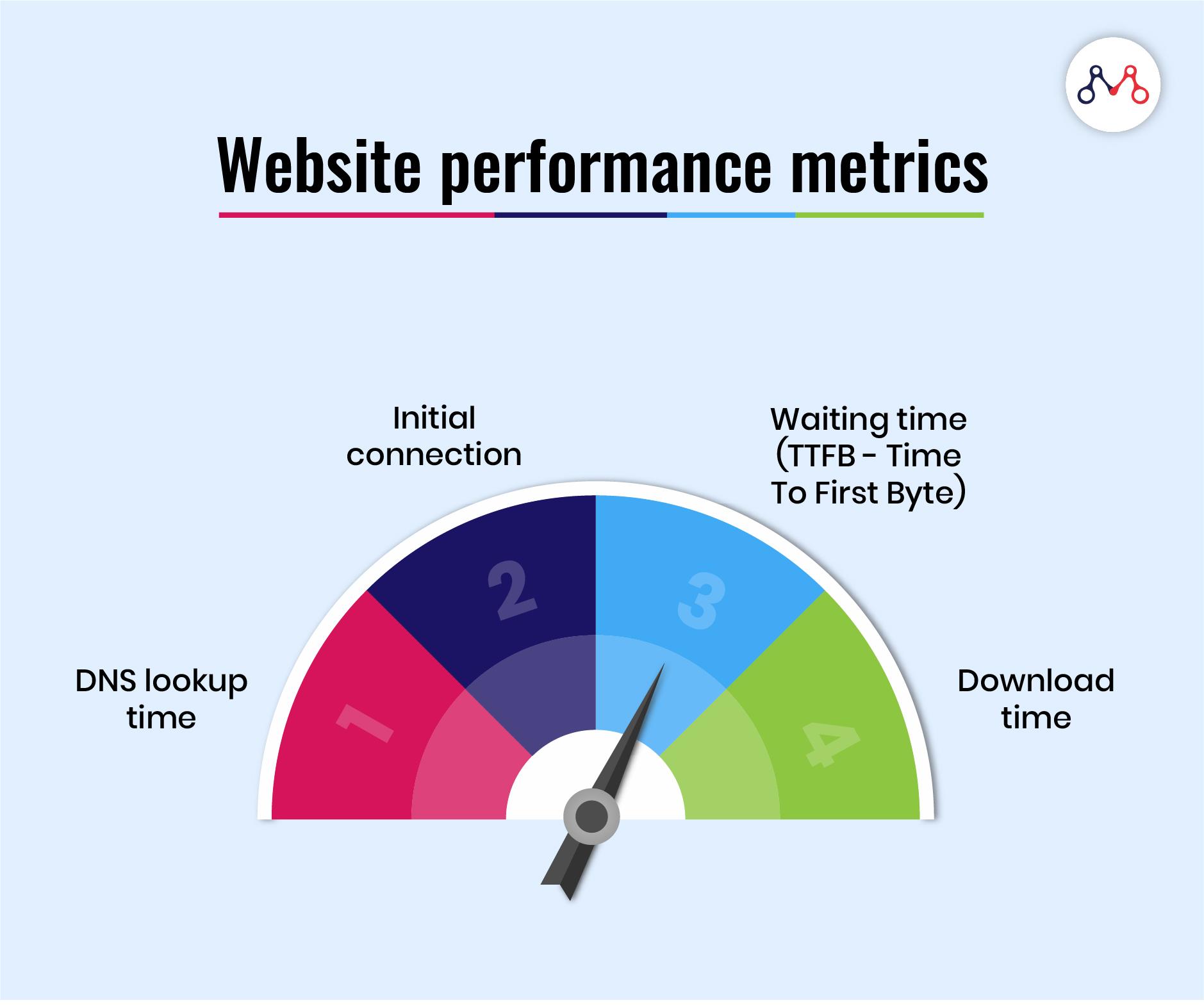
Improving web performance can be a daunting task, especially if you're unfamiliar with common mistakes. From bulky images to messy code, here are 10 pitfalls to avoid for a faster and smoother website experience.
Read more
5 Ways to Improve Website Speed for E-Commerce

Looking to enhance your e-commerce website speed? Check out these 5 tips to help optimize performance and boost user experience for increased conversions and sales.
Read more
How to Spot and Stop a DDoS Attack

As the digital landscape continues to evolve, DDoS attacks have become more prevalent. Learn how to recognize the signs and take action against these malicious threats before they disrupt your online presence.
Read more
Real-Life Applications of Low-Latency Edge Inference

Low-latency edge inference is revolutionizing industries like healthcare, manufacturing, and transportation. From detecting anomalies in medical imaging to optimizing production lines, the possibilities are endless.
Read more










