In the dynamic realm of digital security, protecting APIs against potential threats is paramount. One highly effective method of safeguarding confidential information is through the implementation of JSON Web Token (JWT) validation. This innovative approach not only enhances the overall security of APIs but also ensures a seamless and reliable user authentication process. Let’s delve into the world of JWT validation and explore how it can fortify your API defenses against malicious intruders.
Table of Contents
- Securing APIs: Importance of JWT Validation
- Understanding JSON Web Tokens for API Protection
- Best Practices for Implementing JWT Validation in API Security
- Enhancing API Security with JWT Token Validation
- Q&A
- Future Outlook

Securing APIs: Importance of JWT Validation
When it comes to securing APIs, one of the most important aspects is the validation of JSON Web Tokens (JWTs). JWT validation plays a crucial role in ensuring that only authorized users can access protected resources and services. By verifying the integrity and authenticity of JWTs, developers can prevent unauthorized access and potential security breaches.
Implementing JWT validation involves checking various components of the token, such as the signature, expiration date, issuer, and audience. This process helps to ensure that the token has not been tampered with and is still valid. By incorporating JWT validation into API security measures, developers can enhance the overall protection of their applications and data. Additionally, utilizing JWT validation can help prevent common vulnerabilities, such as token forgery and replay attacks.
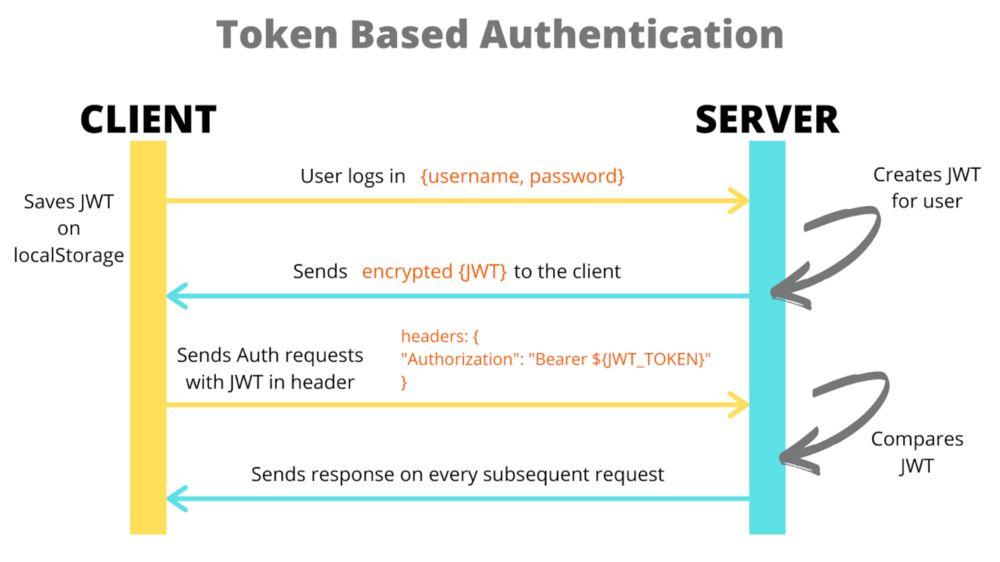
Understanding JSON Web Tokens for API Protection
JSON Web Tokens (JWT) have become a popular method for securing APIs due to their simplicity and flexibility. By using JWT validation, developers can ensure that only authenticated users are able to access protected resources, adding an extra layer of security to their applications.
With JWT validation, API endpoints can easily verify the authenticity of incoming requests by checking the signature of the token. This allows for seamless integration with various authentication methods, such as OAuth2 and OpenID Connect. Additionally, JWTs can carry custom user information in the form of claims, making it easy to personalize and tailor the user experience. Implementing JWT validation is a crucial step in safeguarding APIs against unauthorized access and potential security threats.
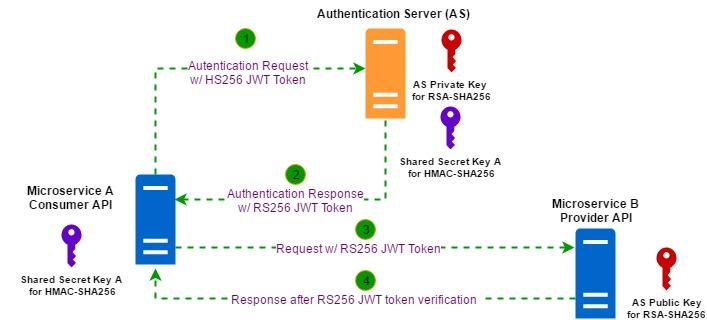
Best Practices for Implementing JWT Validation in API Security
When it comes to API security, implementing JWT validation is a crucial step in ensuring the integrity and authenticity of the data being exchanged. By following best practices for JWT validation, you can significantly reduce the risk of unauthorized access and data breaches. One important aspect to consider is the use of strong encryption algorithms to secure the JWT tokens, such as HMACSHA256 or RSA.
Another key best practice is to carefully validate the JWT tokens before granting access to sensitive data or resources. This includes checking the token’s expiration time, issuer, and signature to ensure its validity. By implementing thorough JWT validation mechanisms, you can enhance the overall security of your APIs and protect against unauthorized access attempts.

Enhancing API Security with JWT Token Validation
JWT (JSON Web Token) validation is a crucial aspect of API security. By implementing JWT token validation, you can enhance the security of your APIs and protect them from unauthorized access. This validation process involves verifying the integrity and authenticity of tokens before allowing access to protected resources.
One of the key benefits of using JWT token validation is its ability to prevent token tampering and ensure that only authenticated users can access your APIs. By incorporating this security measure, you can mitigate the risk of unauthorized access and protect sensitive data from potential threats. Additionally, JWT validation helps to enforce secure communication between clients and servers, adding an extra layer of protection to your API infrastructure.
Q&A
Q: What is JWT validation and why is it important for protecting APIs?
A: JWT validation is a process of verifying the authenticity of JSON Web Tokens (JWT) to ensure that only authorized users have access to APIs. It is crucial for protecting APIs from unauthorized access and data breaches.
Q: How does JWT validation work?
A: JWT validation involves checking the signature, expiration date, issuer, and other claims in a JWT to confirm its validity. This process helps ensure that the token has not been tampered with and is being used by the intended recipient.
Q: What are the benefits of using JWT validation for API security?
A: Using JWT validation for API security helps prevent unauthorized access, data theft, and other malicious activities. It also allows organizations to implement fine-grained access control and secure communication between clients and servers.
Q: Are there any potential drawbacks or challenges to implementing JWT validation?
A: Implementing JWT validation may require additional development effort and expertise. Organizations also need to securely store and manage JWT secret keys to prevent unauthorized access to APIs.
Q: How can organizations effectively protect APIs with JWT validation?
A: Organizations can effectively protect APIs with JWT validation by following best practices such as using strong encryption algorithms, regularly rotating secret keys, and implementing proper access control mechanisms. It is also important to monitor and audit API access to detect and respond to any security incidents.
Future Outlook
implementing JWT validation is a crucial step in safeguarding your APIs and ensuring their security against potential threats. By leveraging the power of JSON Web Tokens, you can authenticate and authorize users with confidence, while also maintaining a seamless and efficient user experience. So don’t wait any longer, take the necessary measures to protect your APIs today and keep your data safe from prying eyes. Thank you for reading!










