A look at the latest post-quantum signature standardization candidates

Explore the cutting-edge world of post-quantum cryptography with a look at the newest signature standardization candidates. The race to secure our digital future is on!
Read more
Introducing Access for Infrastructure: SSH
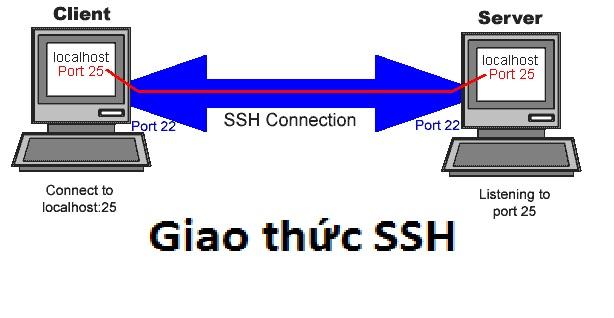
Access for Infrastructure simplifies remote server management with SSH. It provides secure access to servers, ensuring efficient deployment and maintenance.
Read more
Cloudflare’s URL Scanner, new features, and the story of how we built it

Discover the fascinating story behind the creation of Cloudflare's innovative URL Scanner. Learn about the new features that make this tool a game-changer in website security. Join us on a journey of innovation and technology.
Read more
Introducing Ephemeral IDs: a new tool for fraud detection
Introducing Ephemeral IDs: the innovative new tool that is revolutionizing fraud detection. Say goodbye to traditional methods and hello to enhanced security with this cutting-edge technology.
Read more
Introducing Automatic SSL/TLS: securing and simplifying origin connectivity
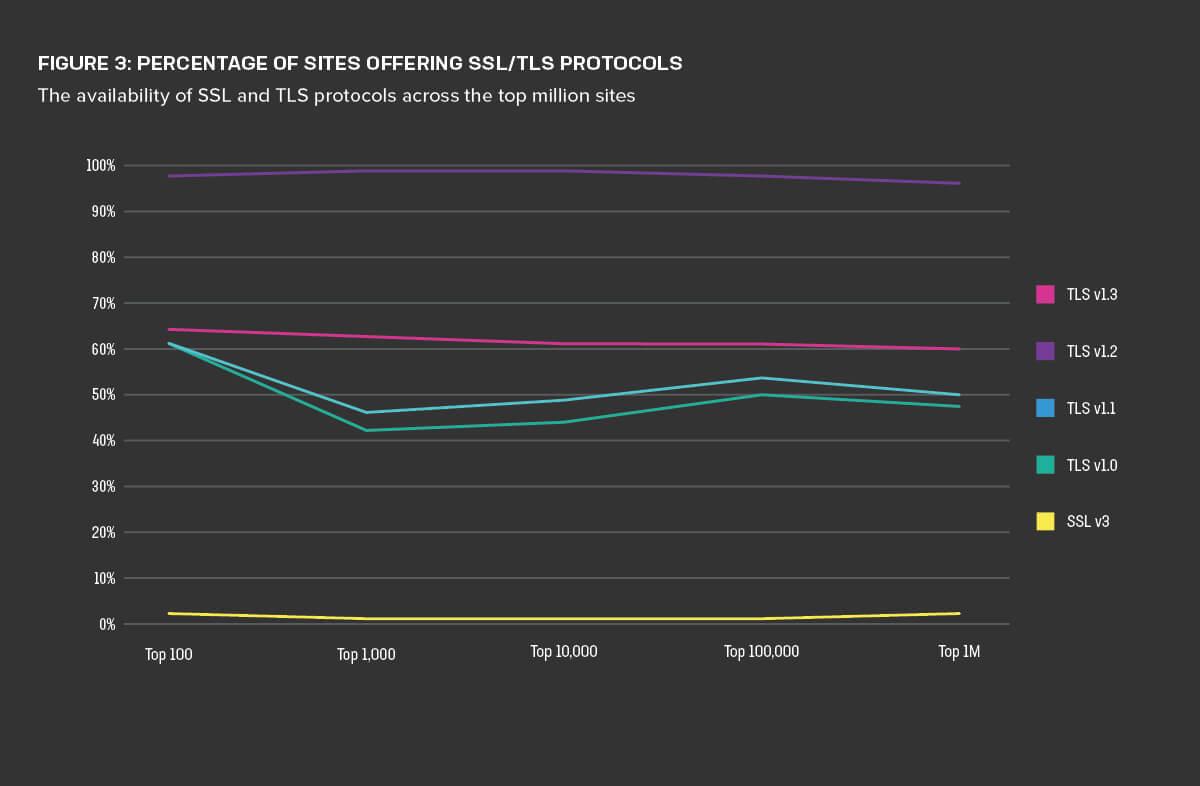
In the ever-evolving landscape of cybersecurity, the introduction of Automatic SSL/TLS is revolutionizing the way we secure and simplify origin connectivity. With this game-changing technology, organizations can rest assured that their data is protected without the hassle of manual configurations.
Read more